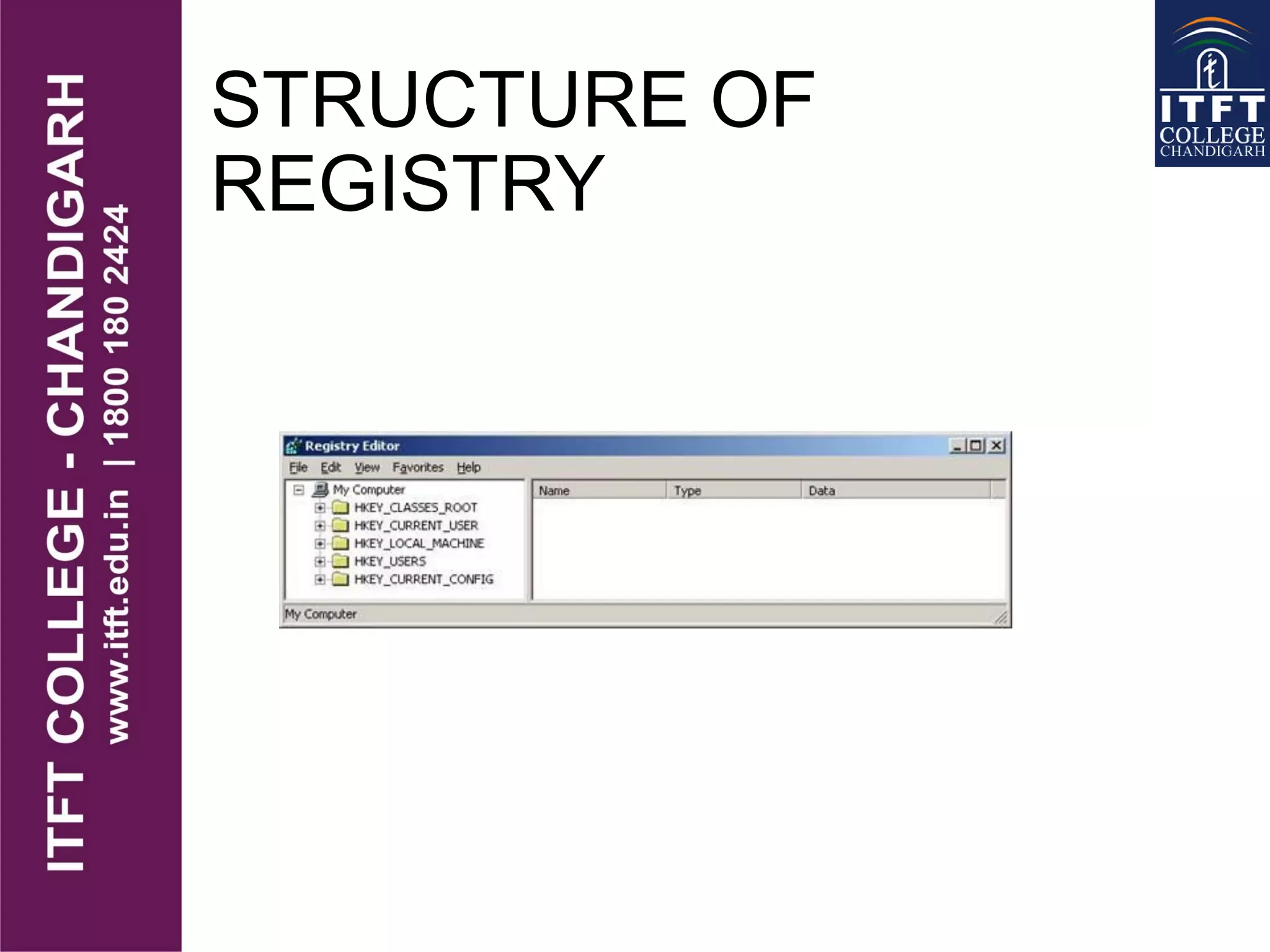
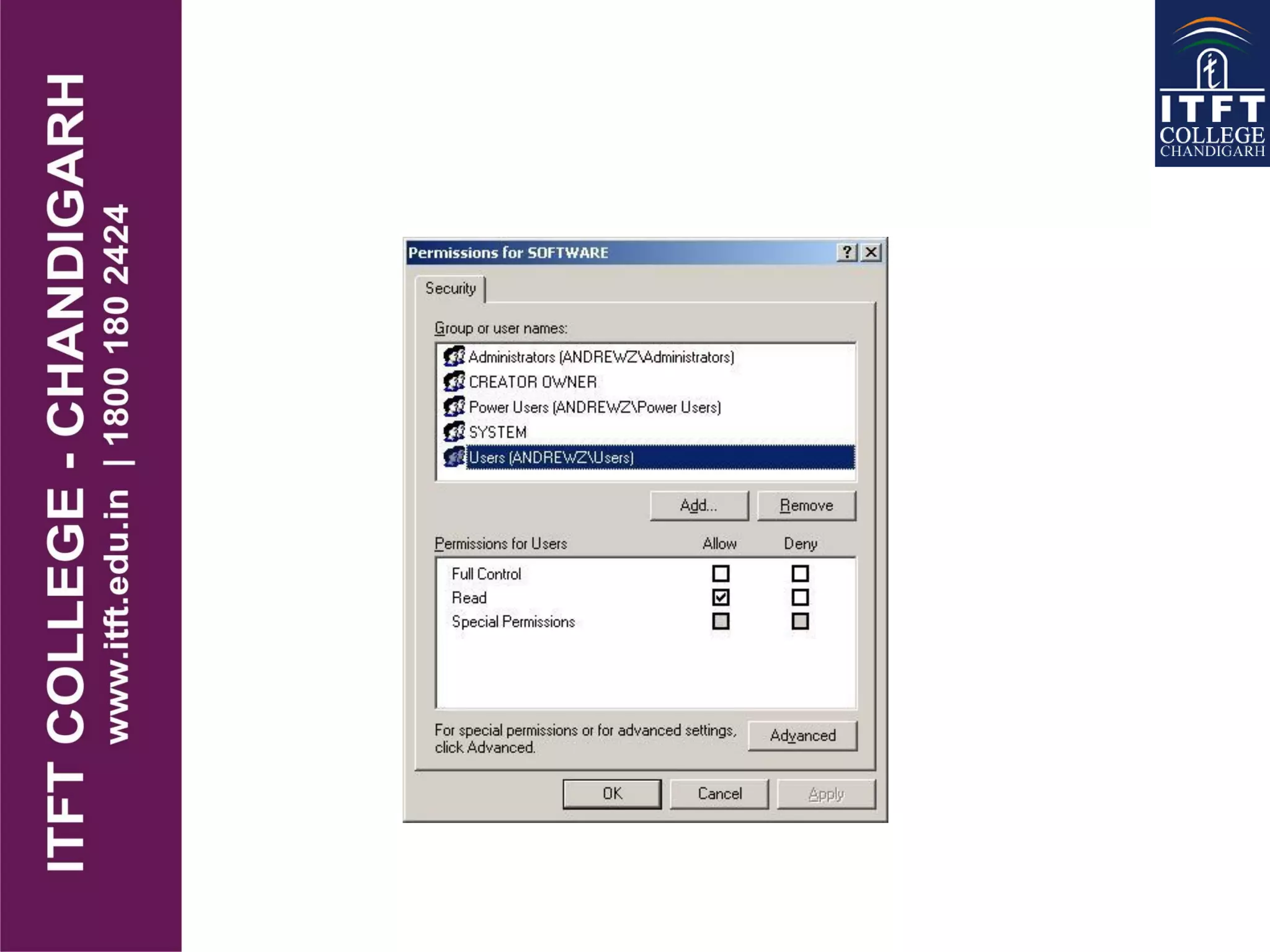
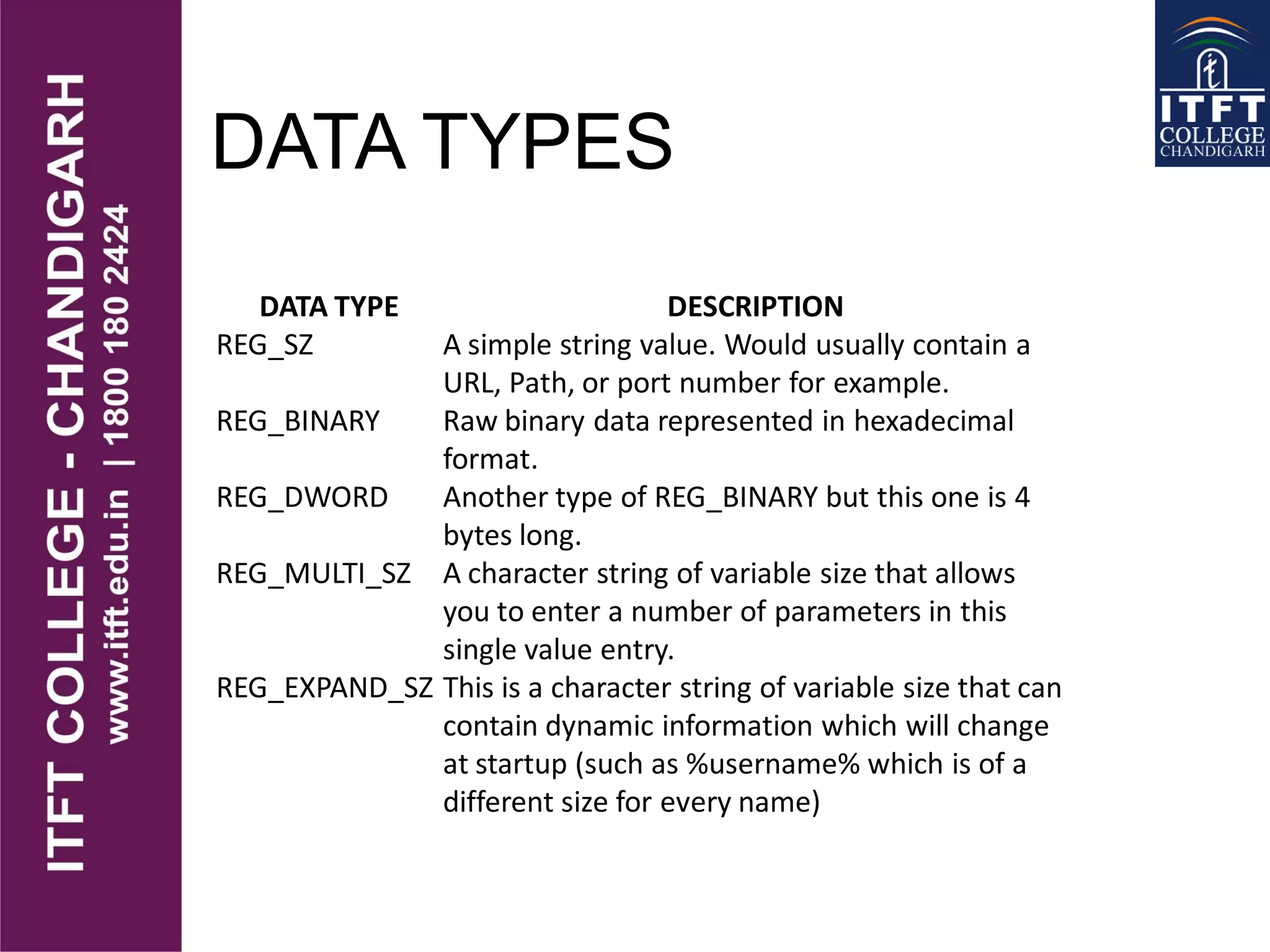
The document discusses various network protocols supported by Windows NT and factors to consider when choosing a protocol. It provides details on NetBEUI, NWLink, and TCP/IP protocols, describing what each is used for and their relative requirements and limitations. It also covers the structure and purpose of the Windows registry, which stores configuration settings in a central location replacing older .INI files.