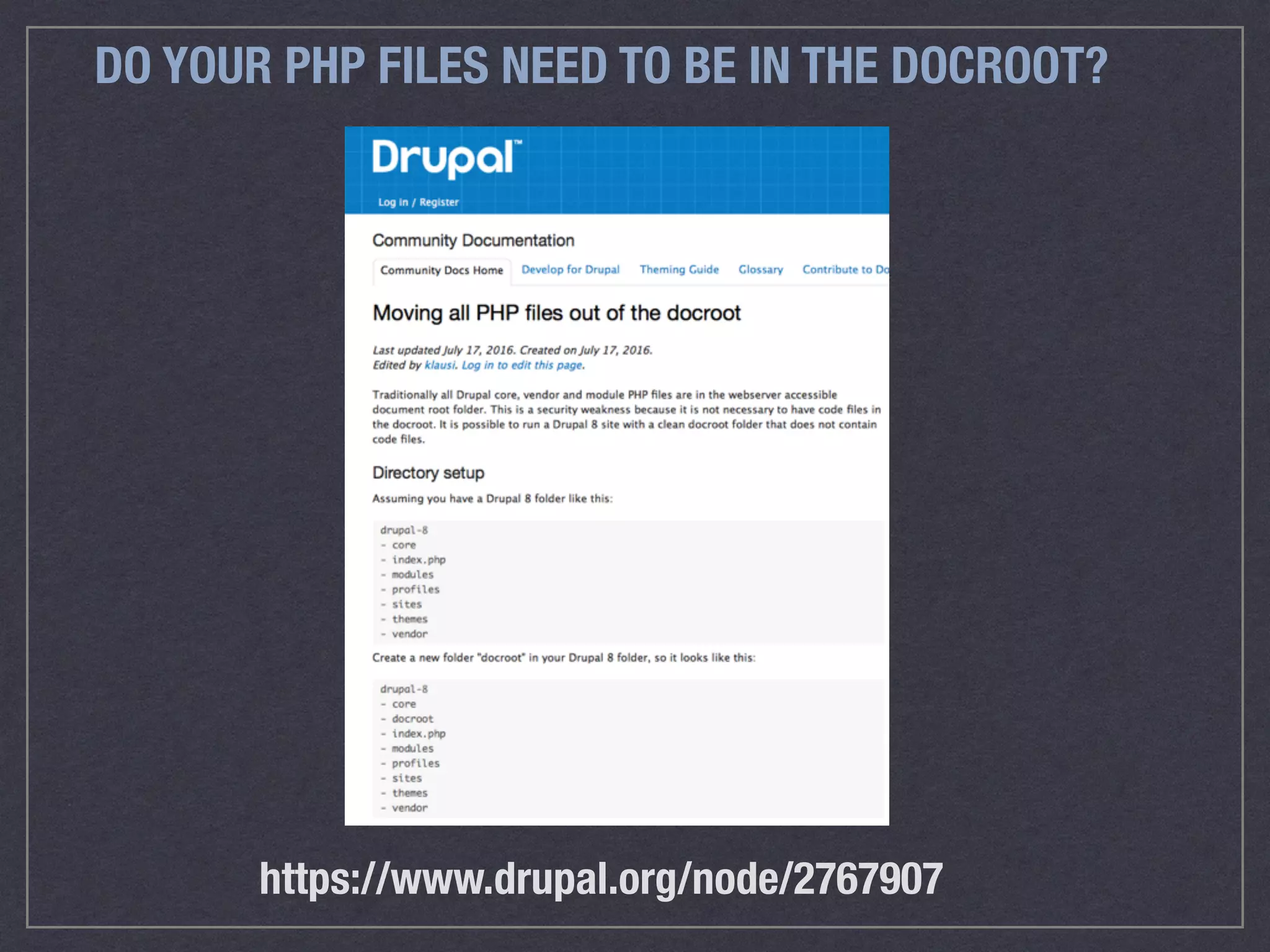
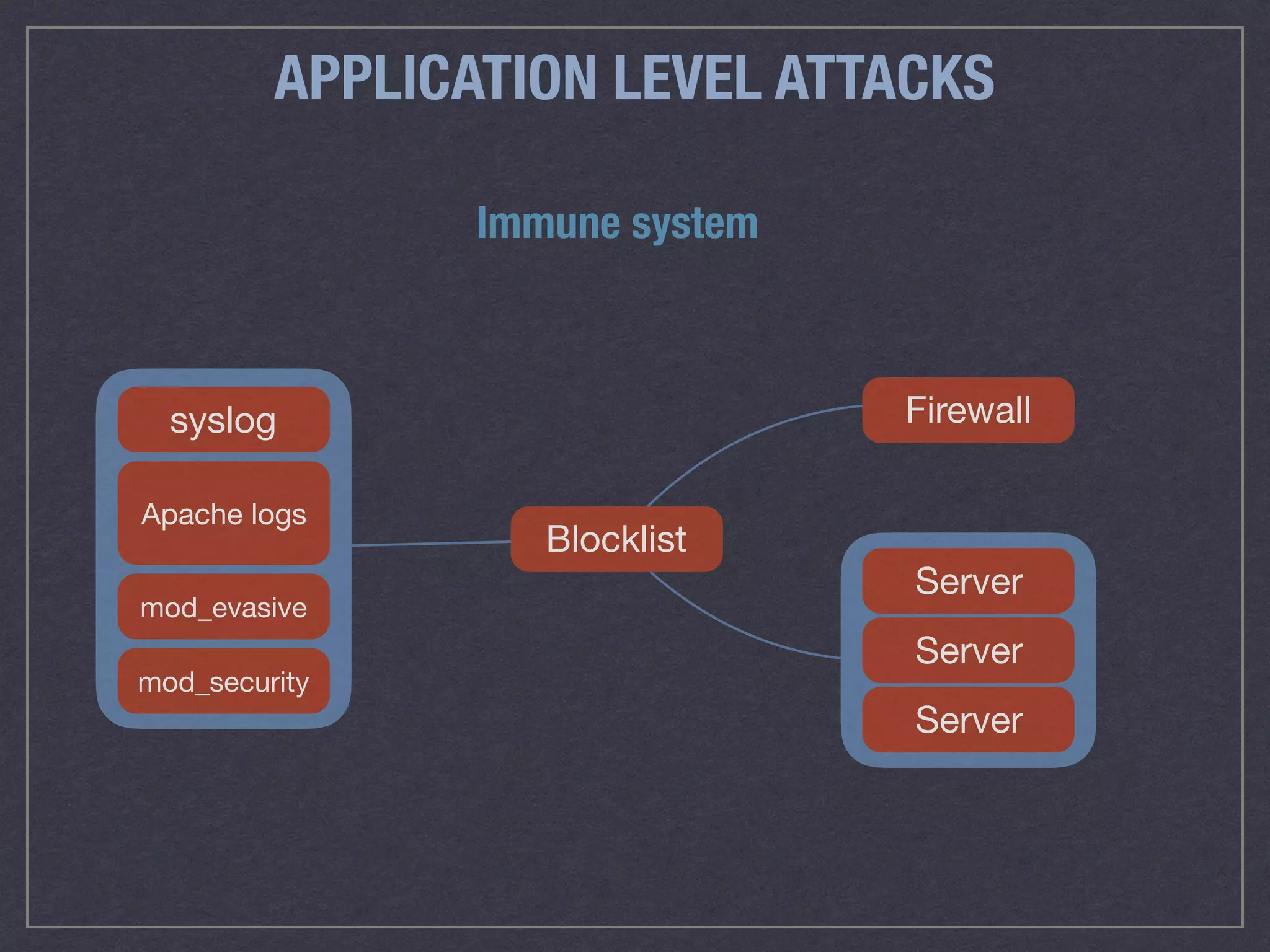
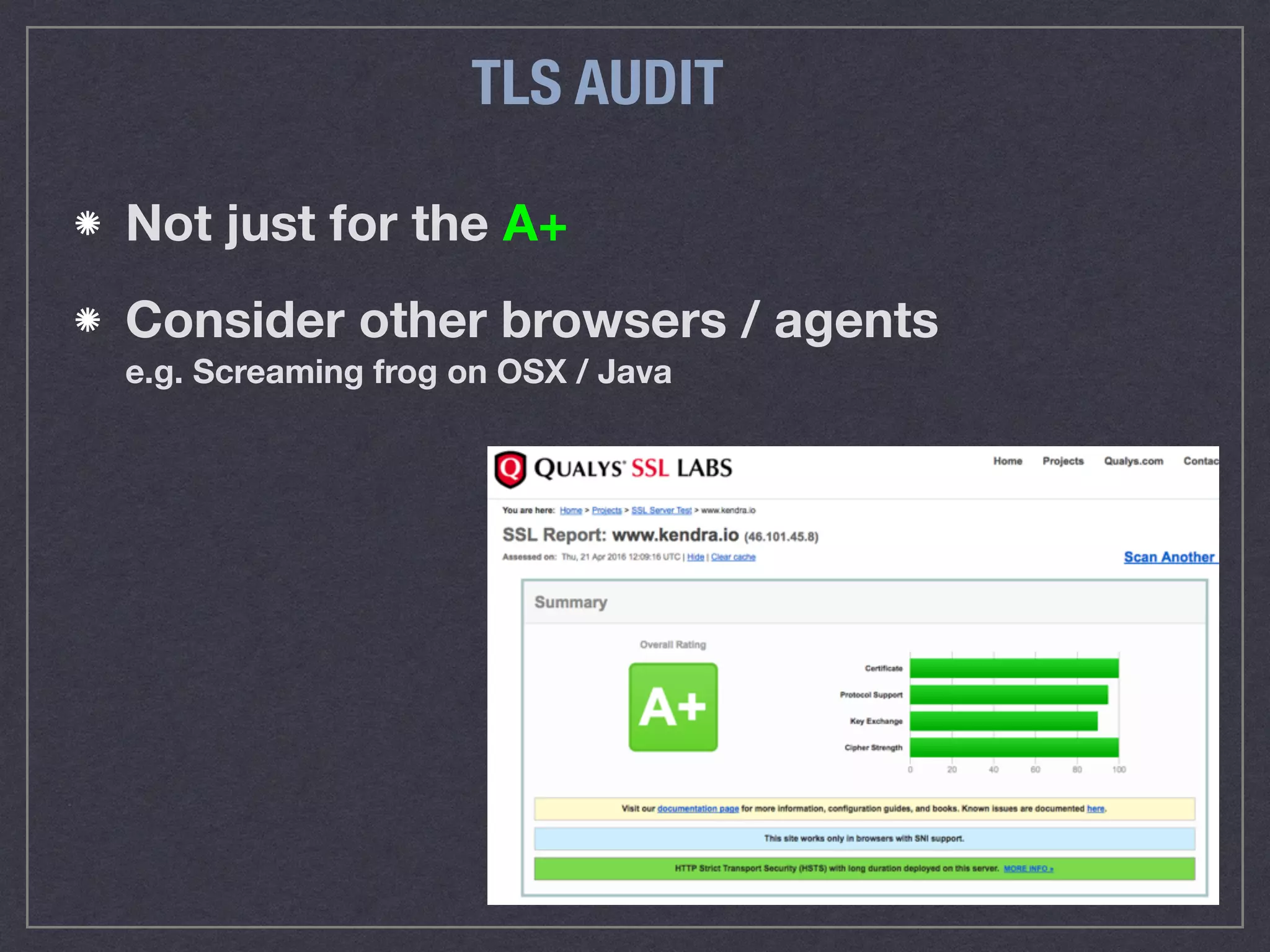
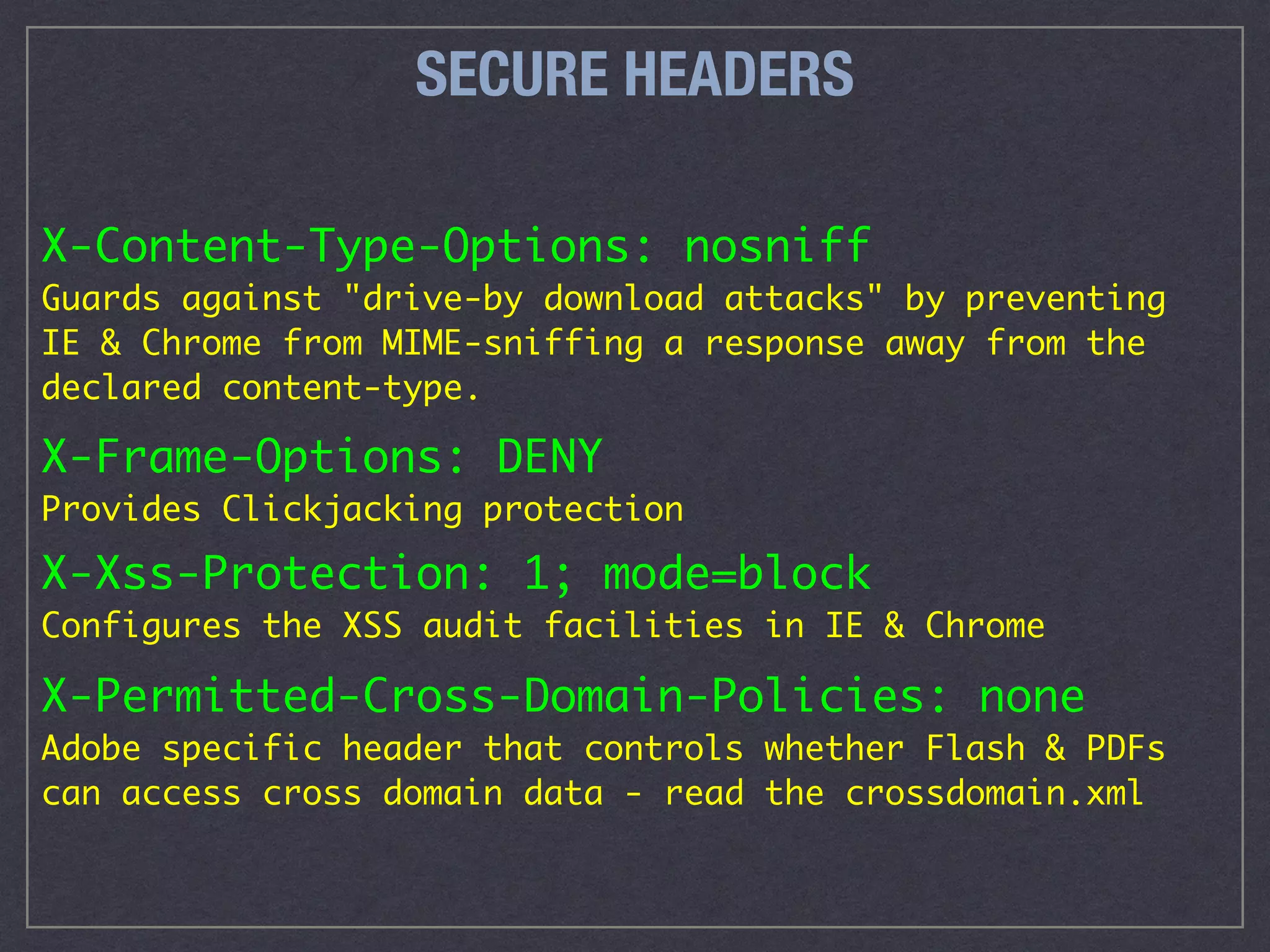
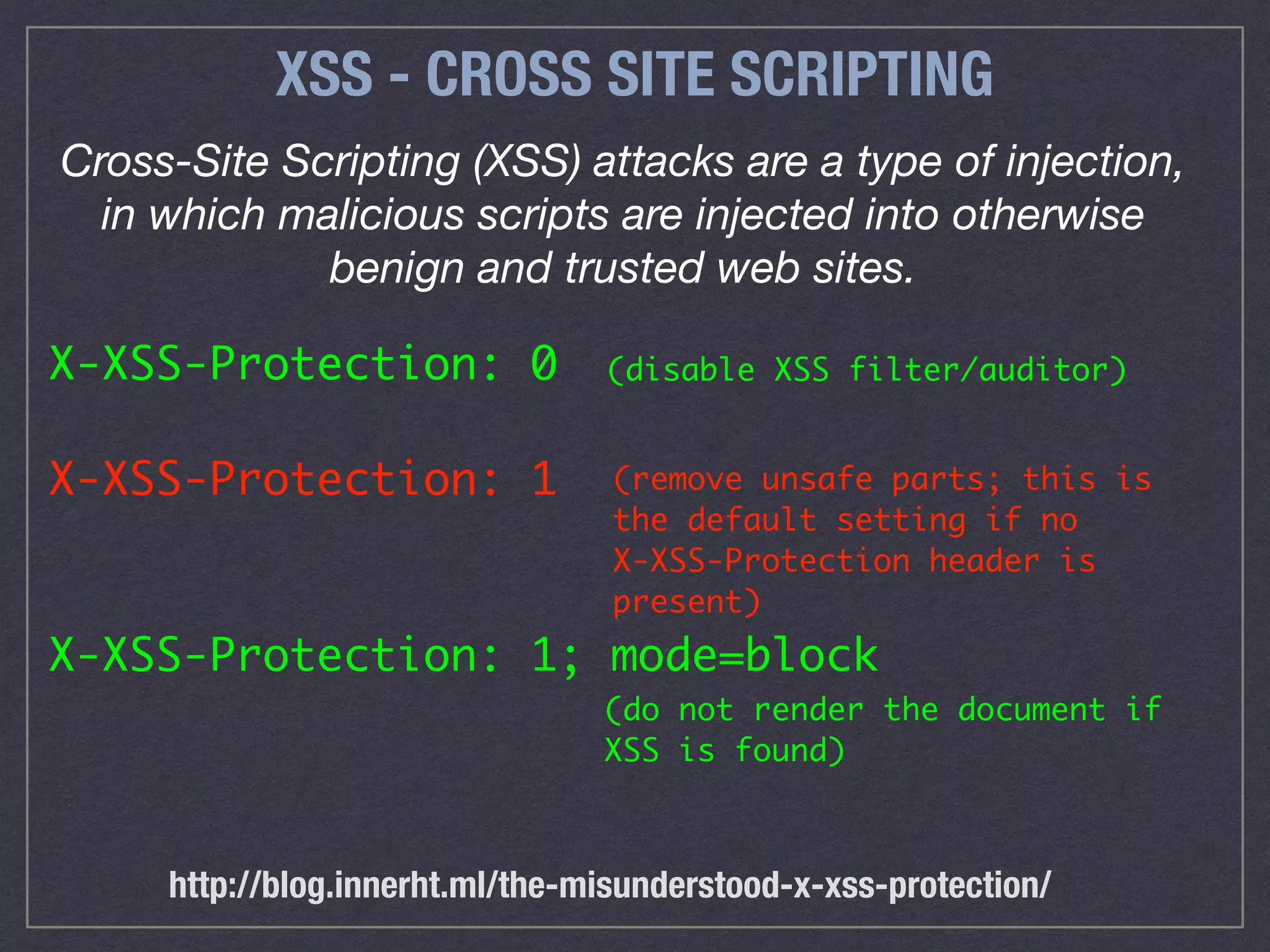
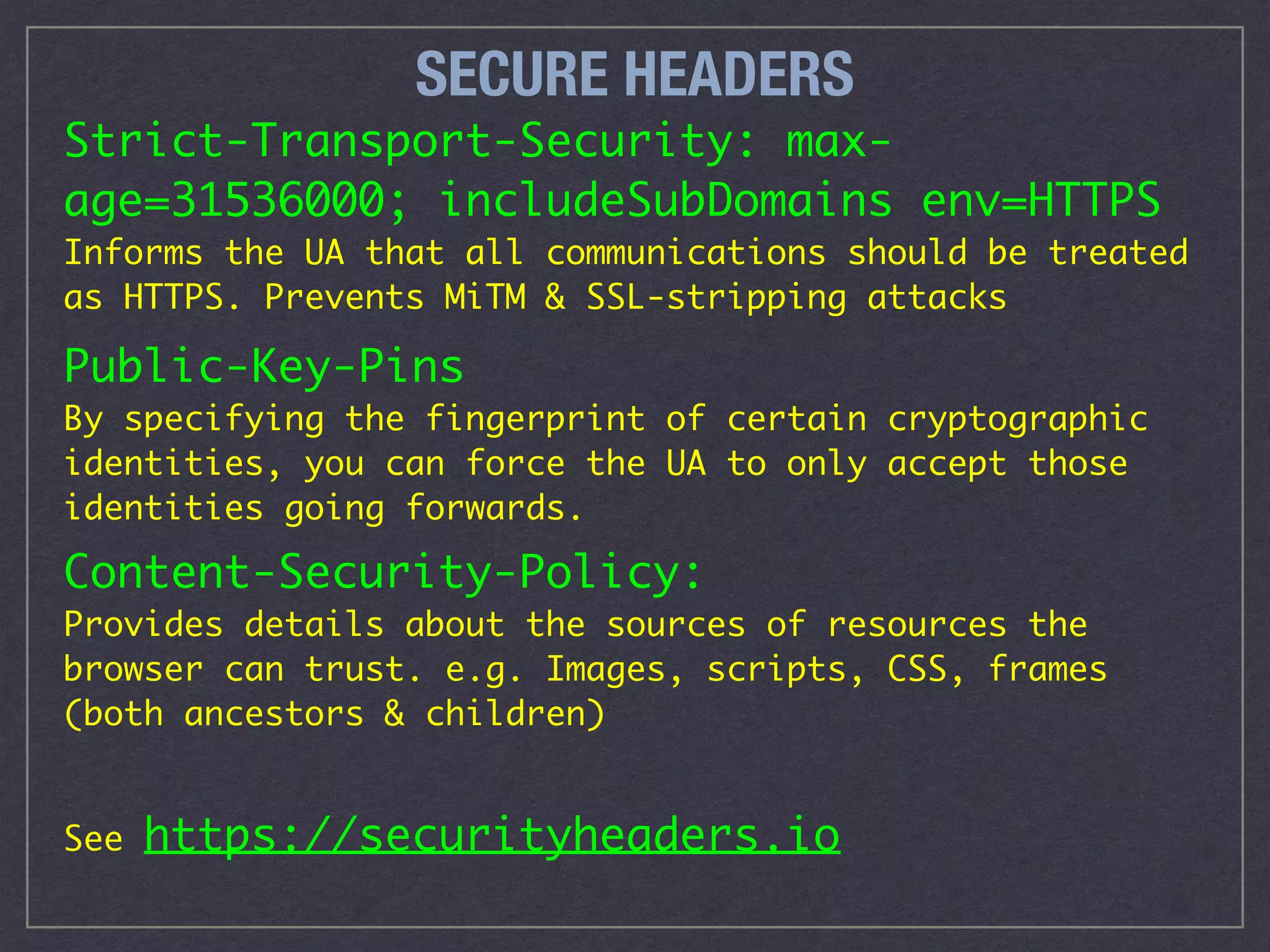
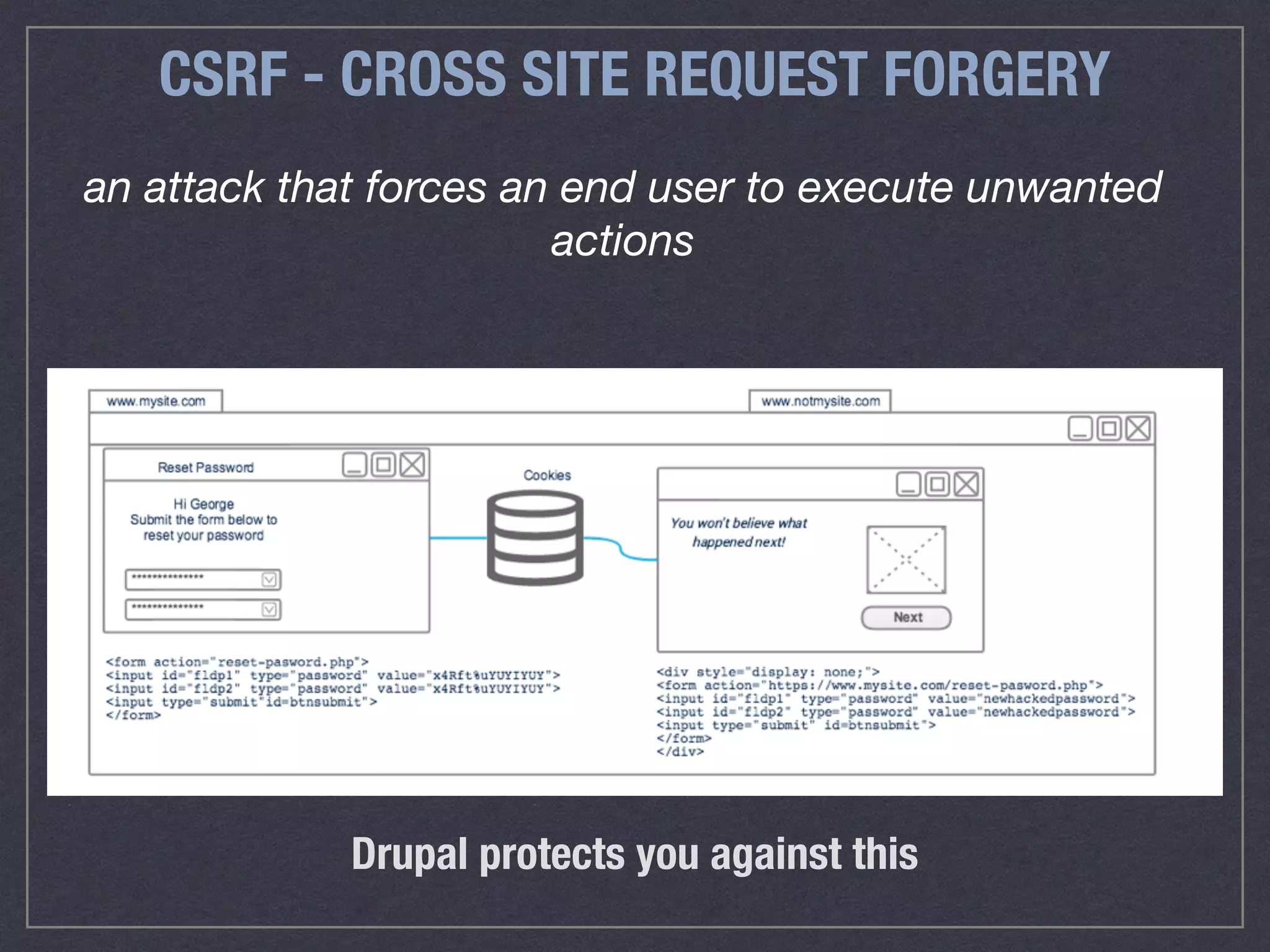
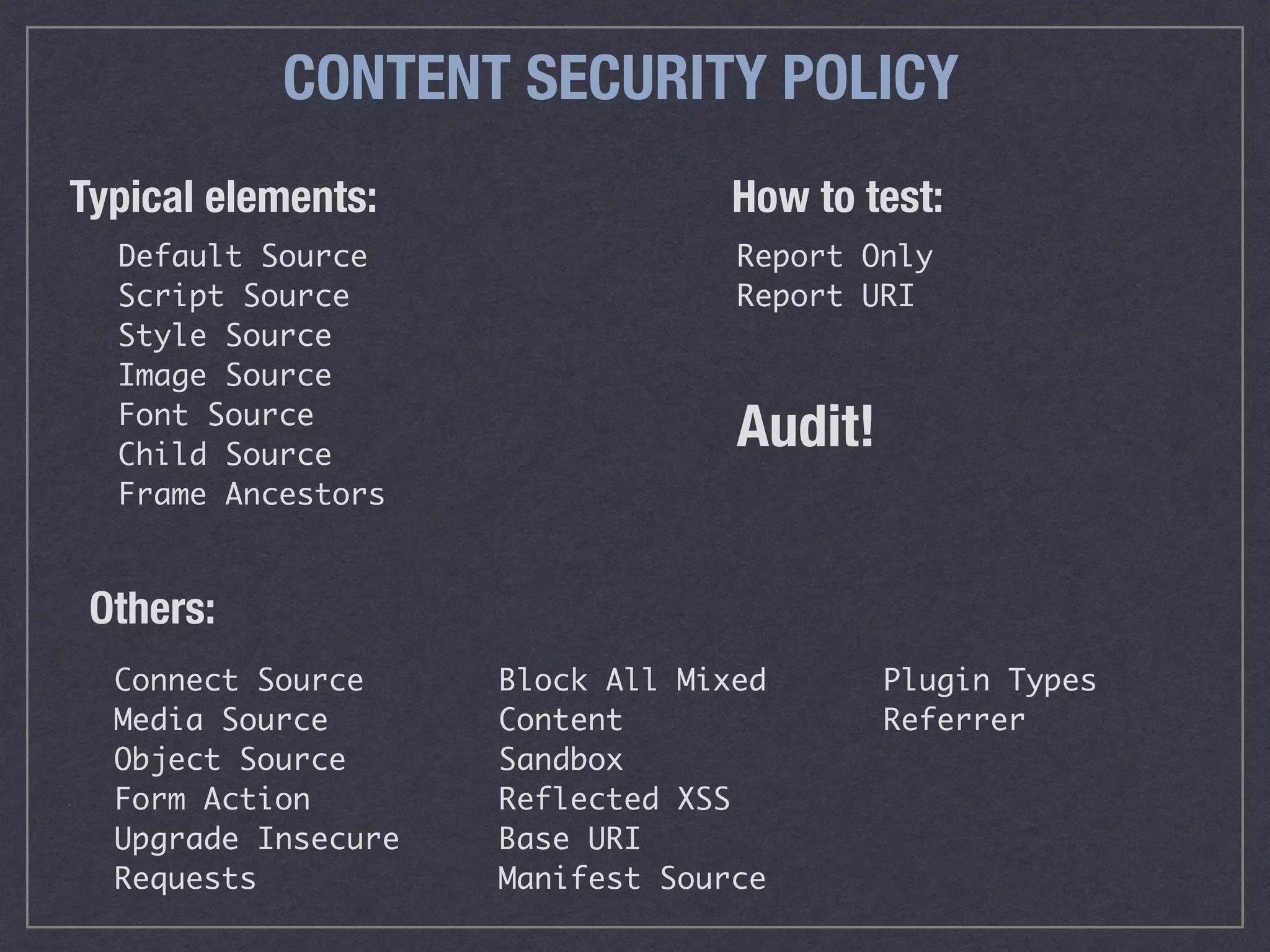
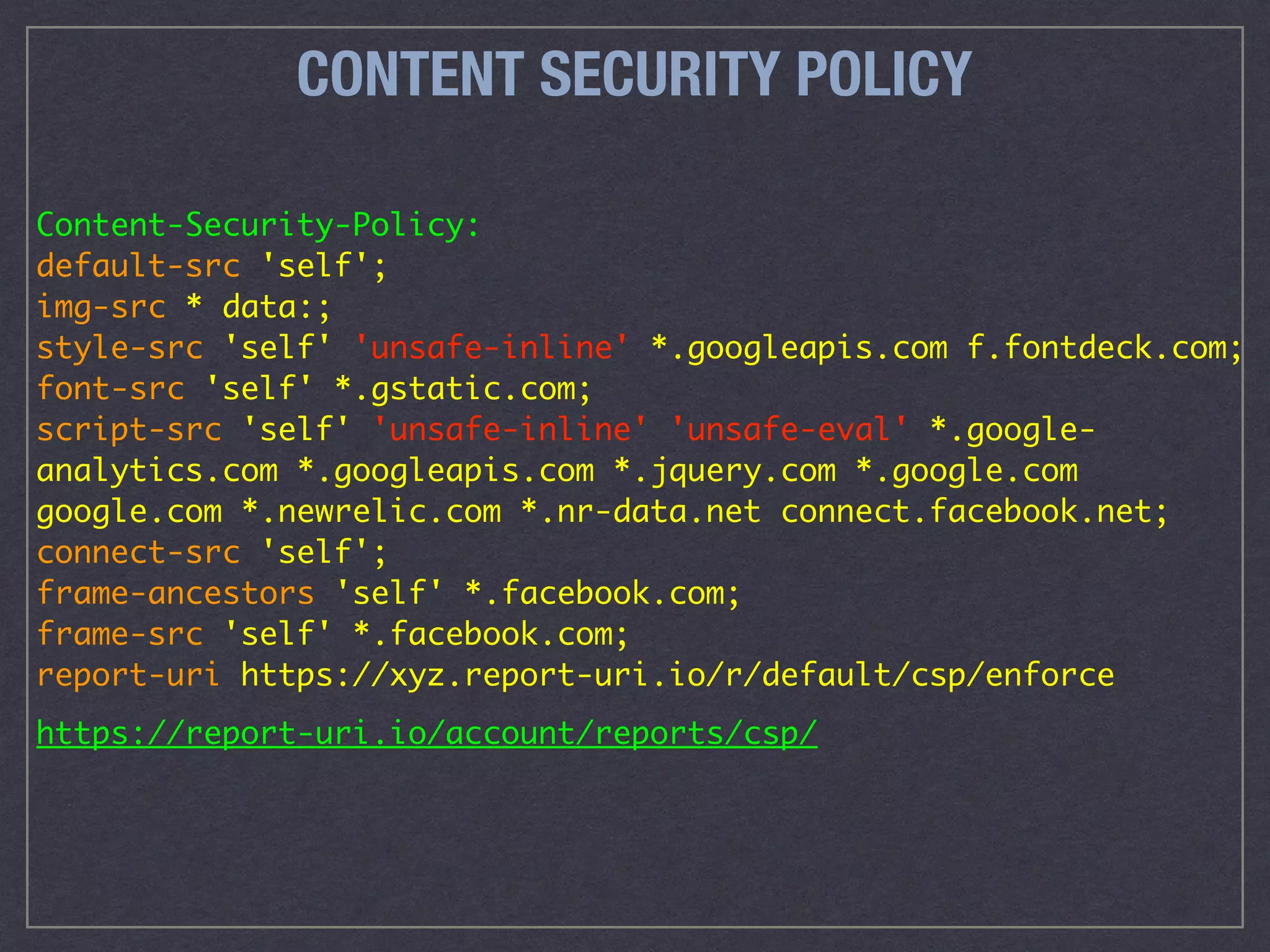
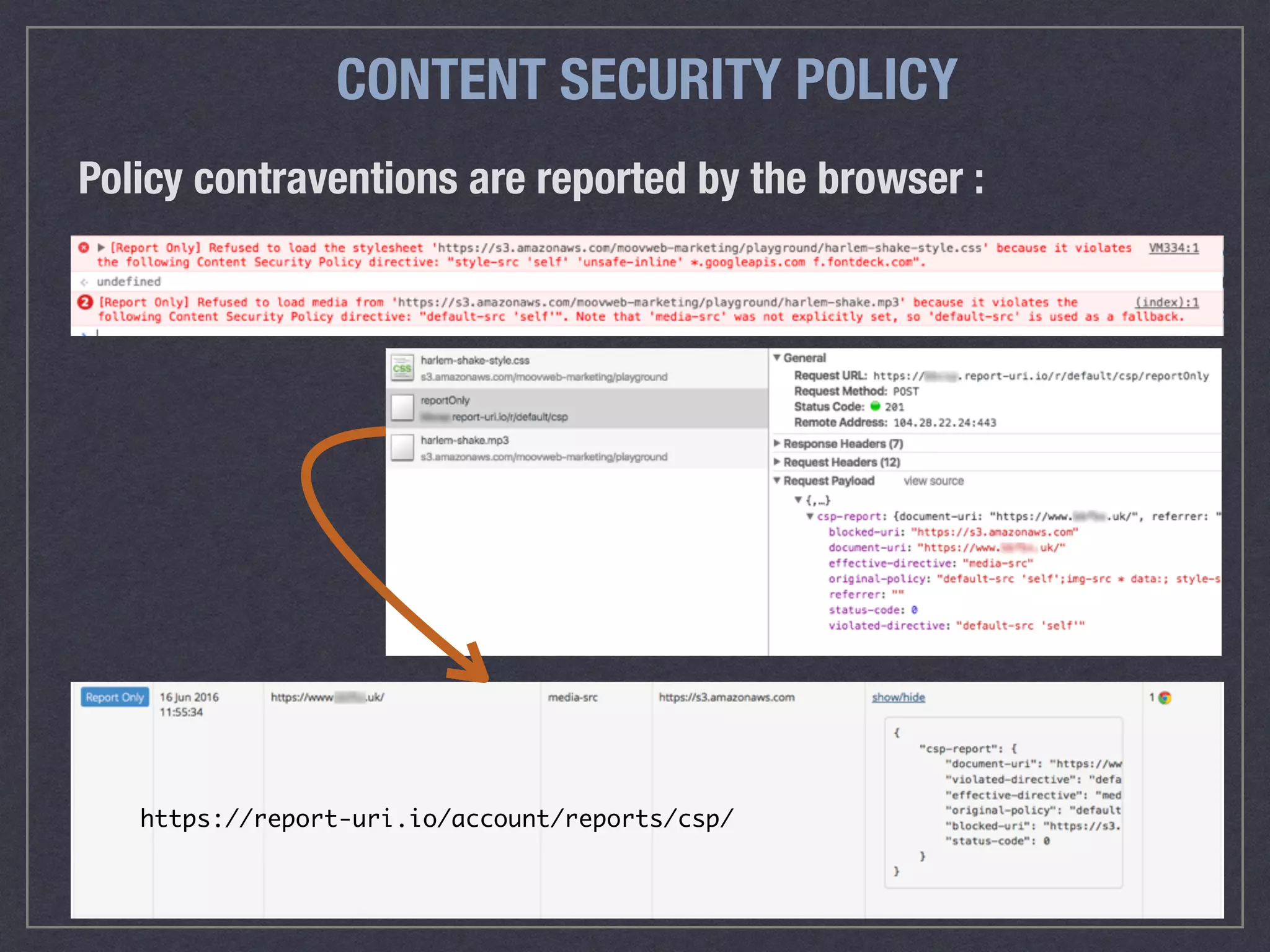
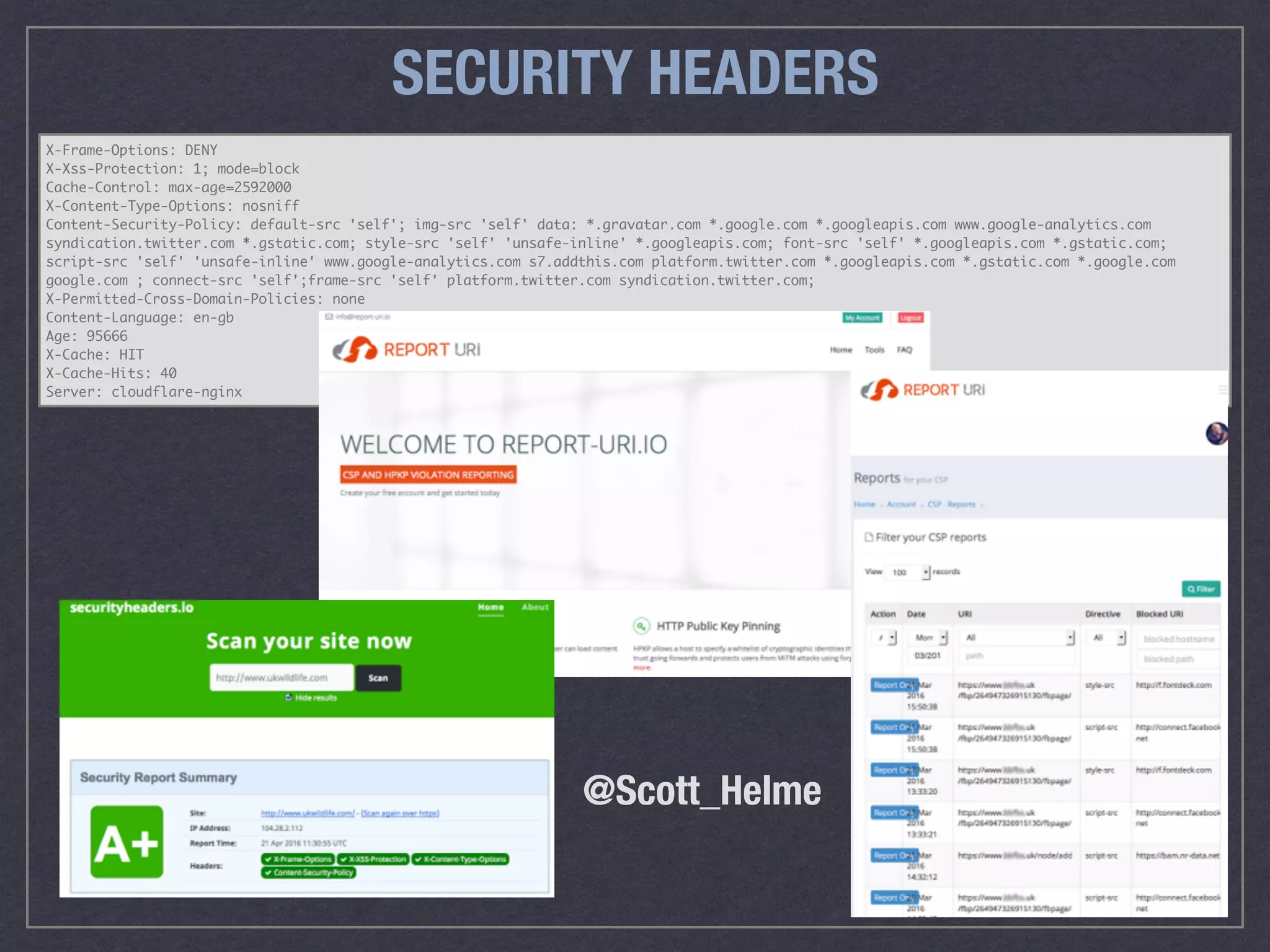
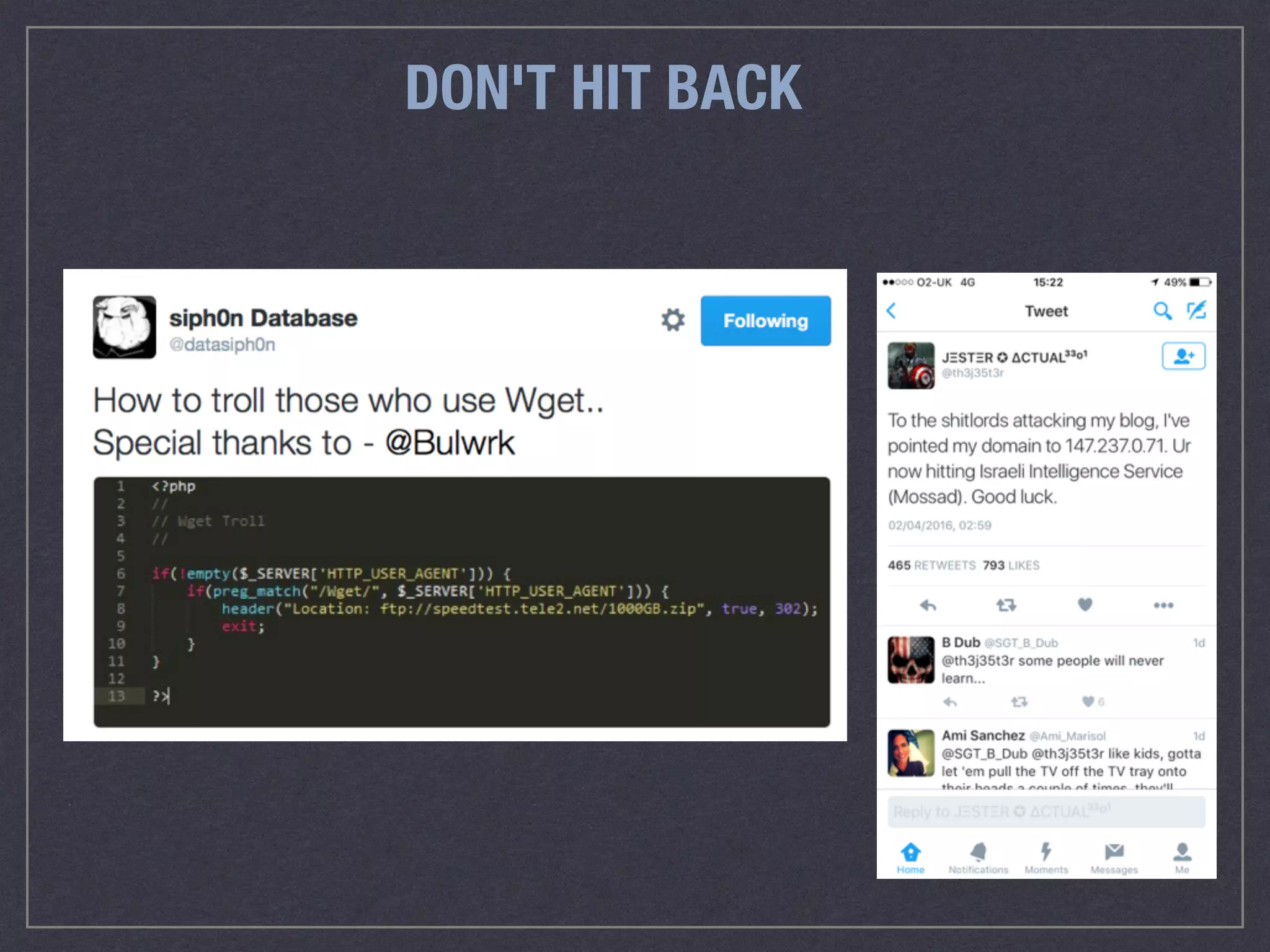
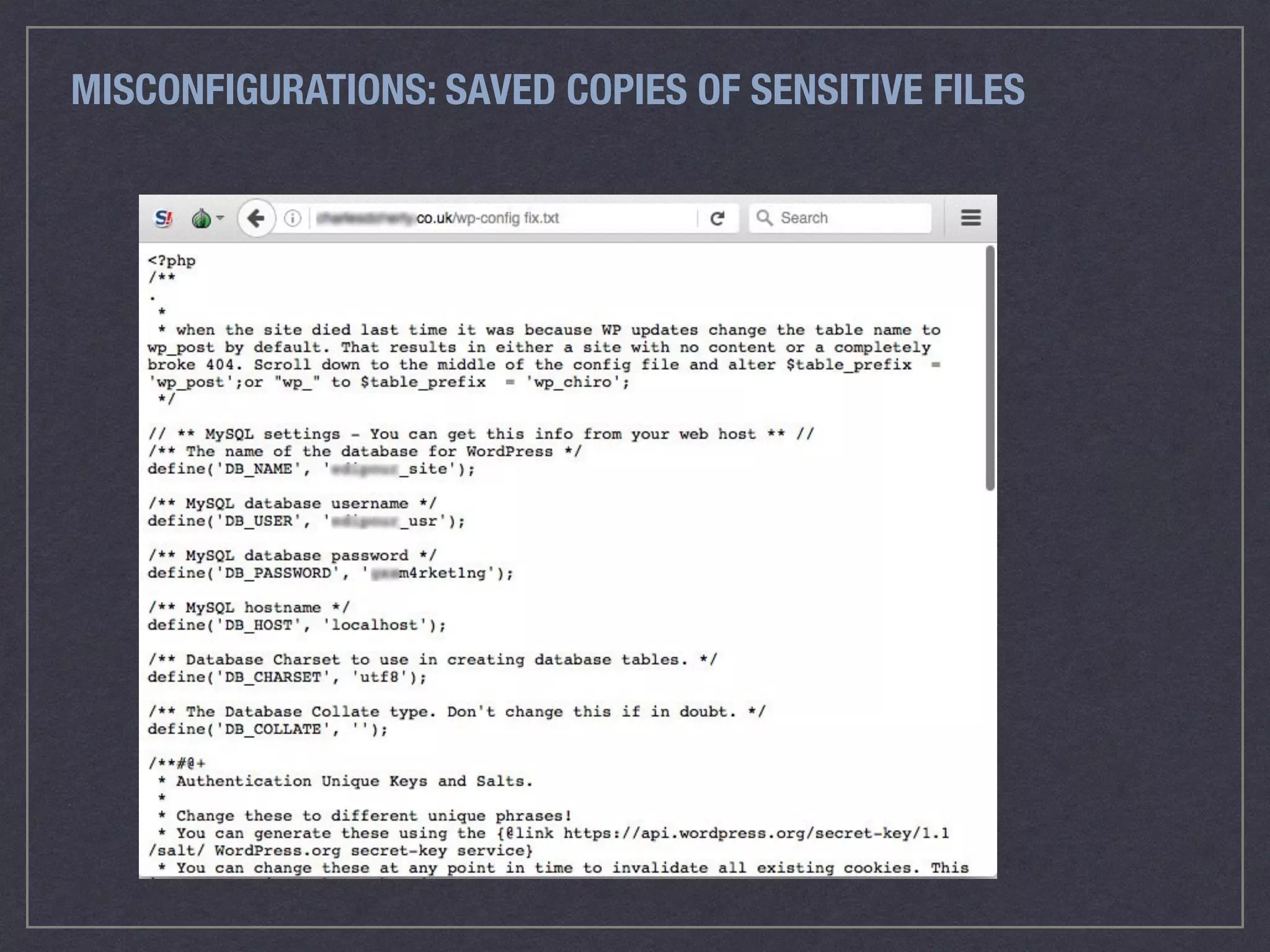
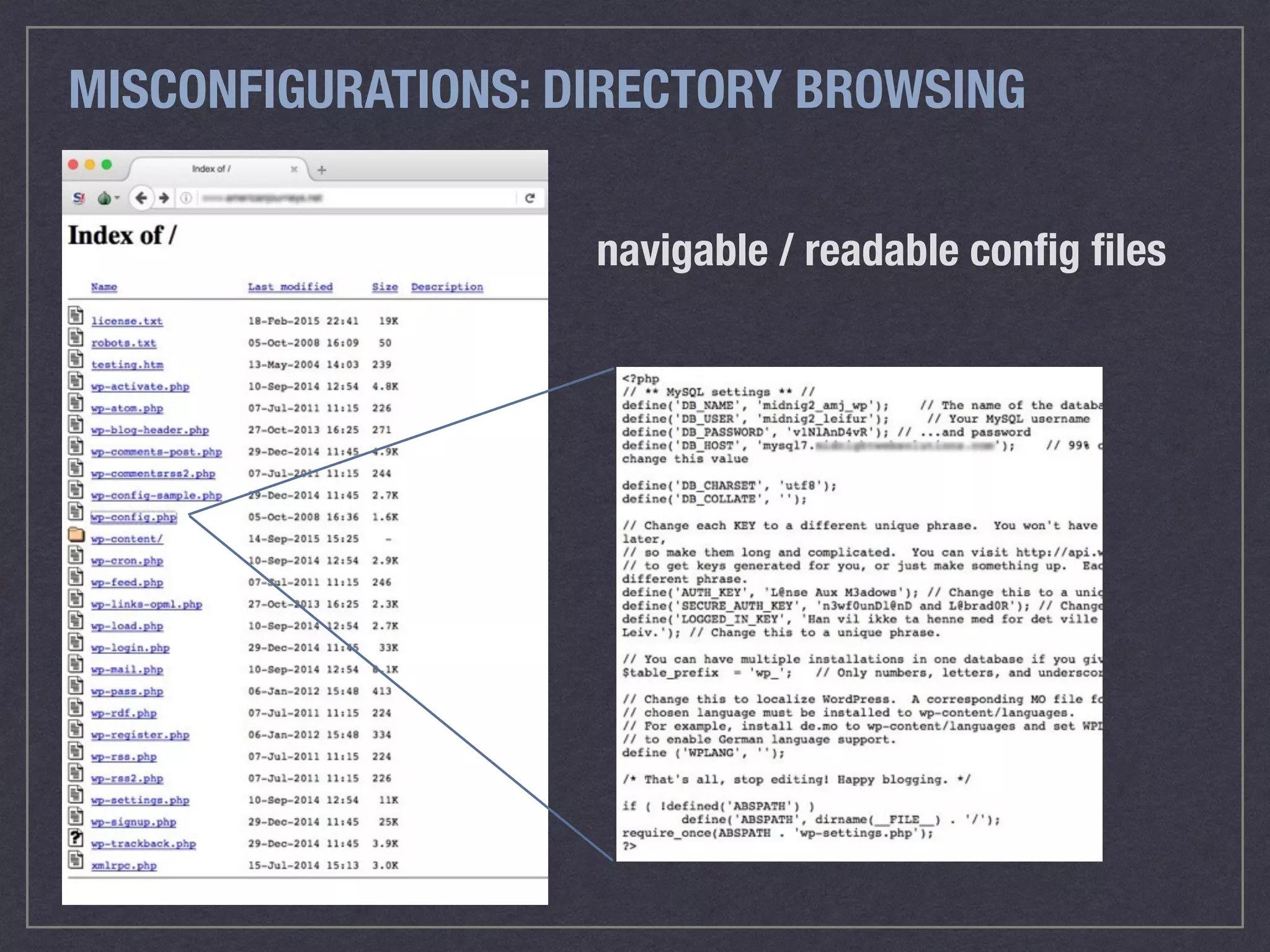
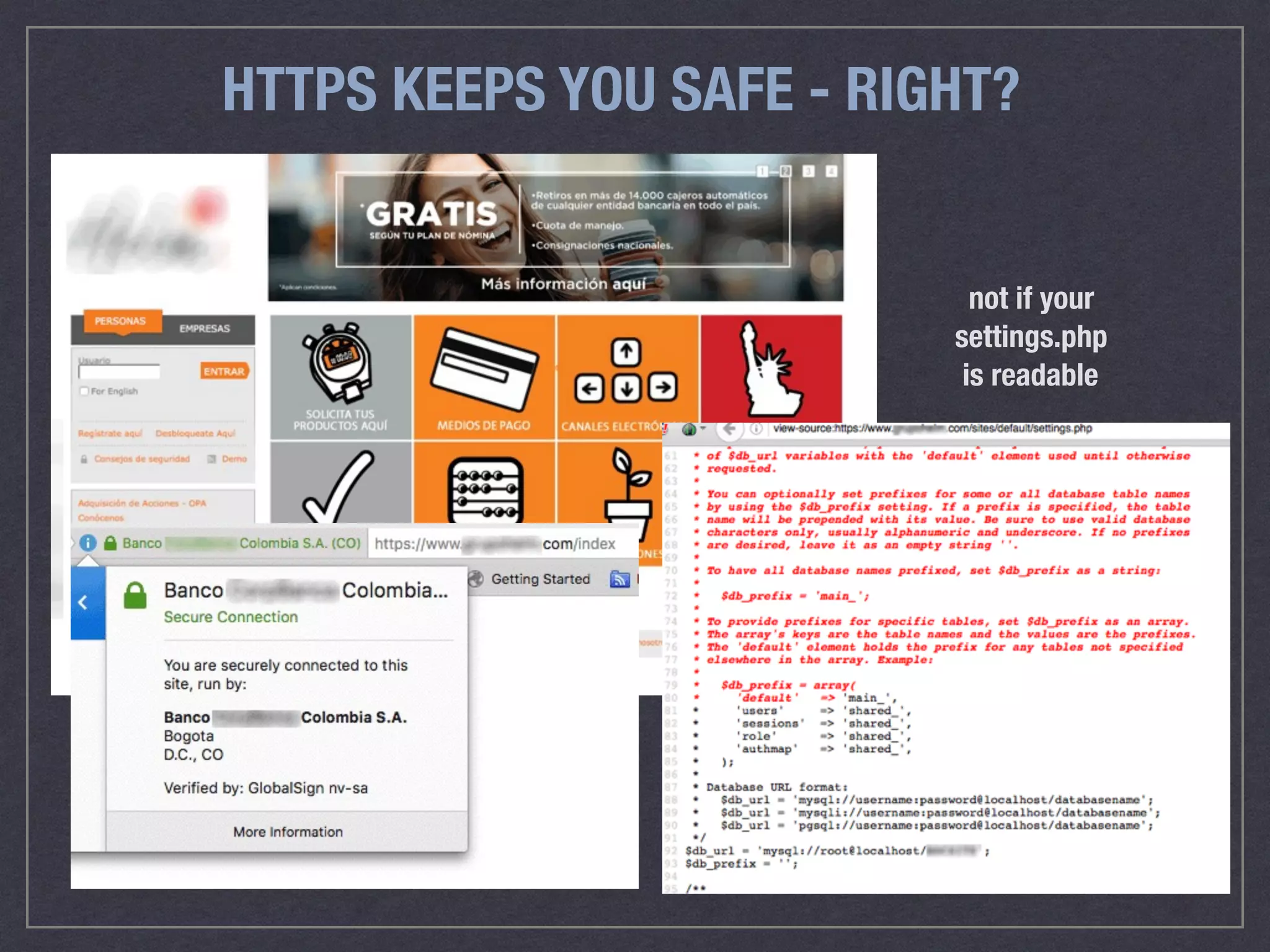
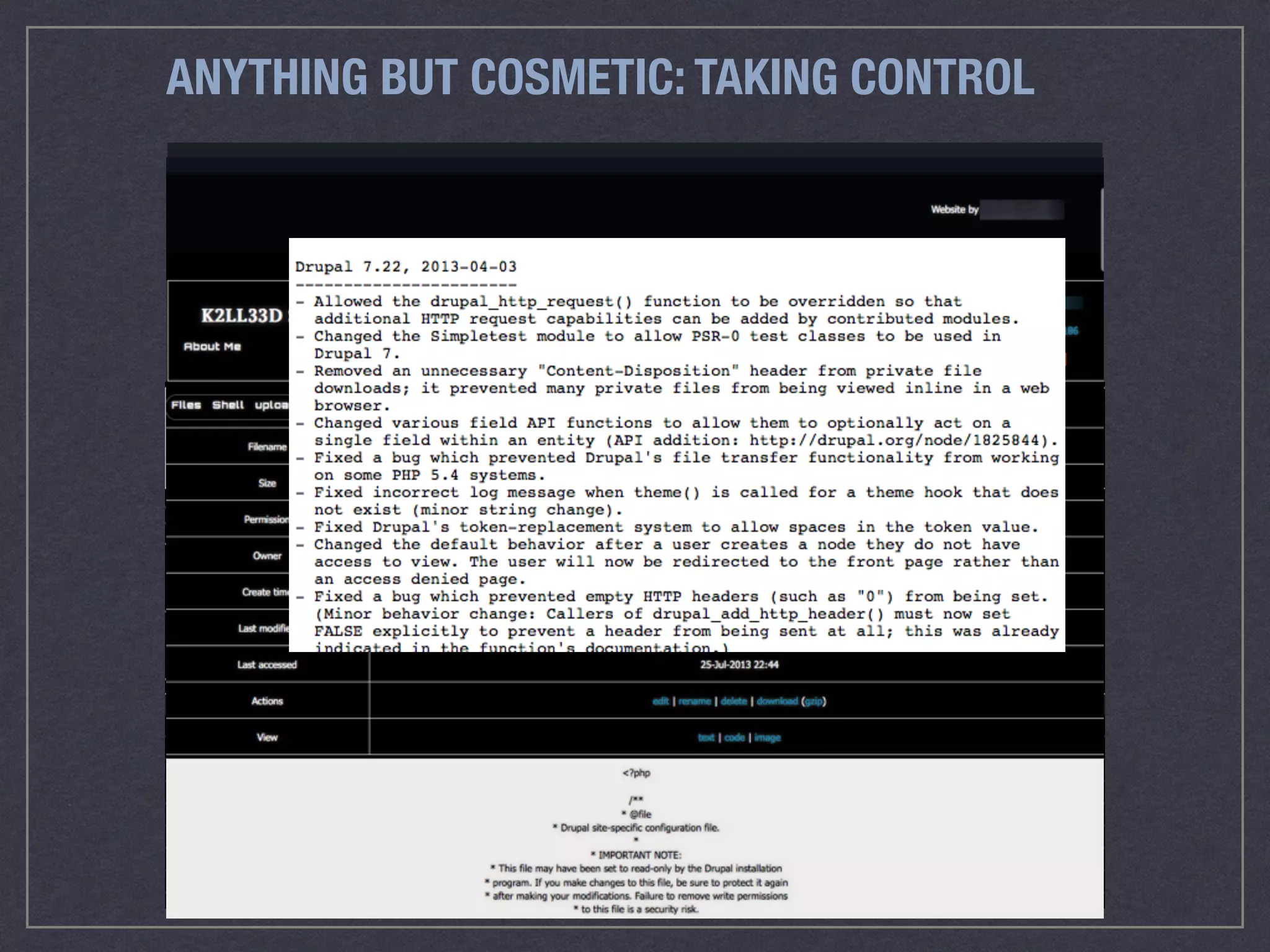
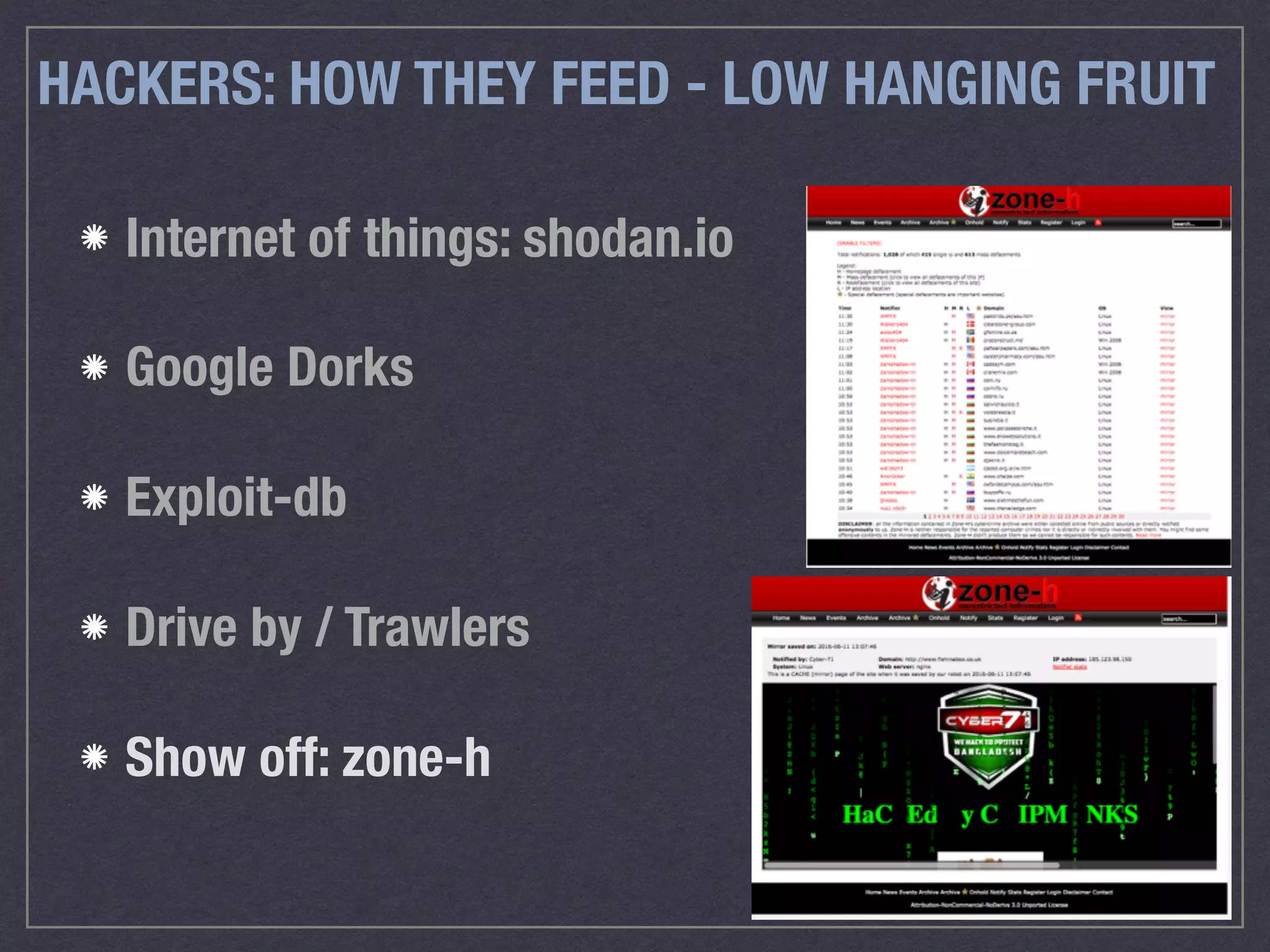
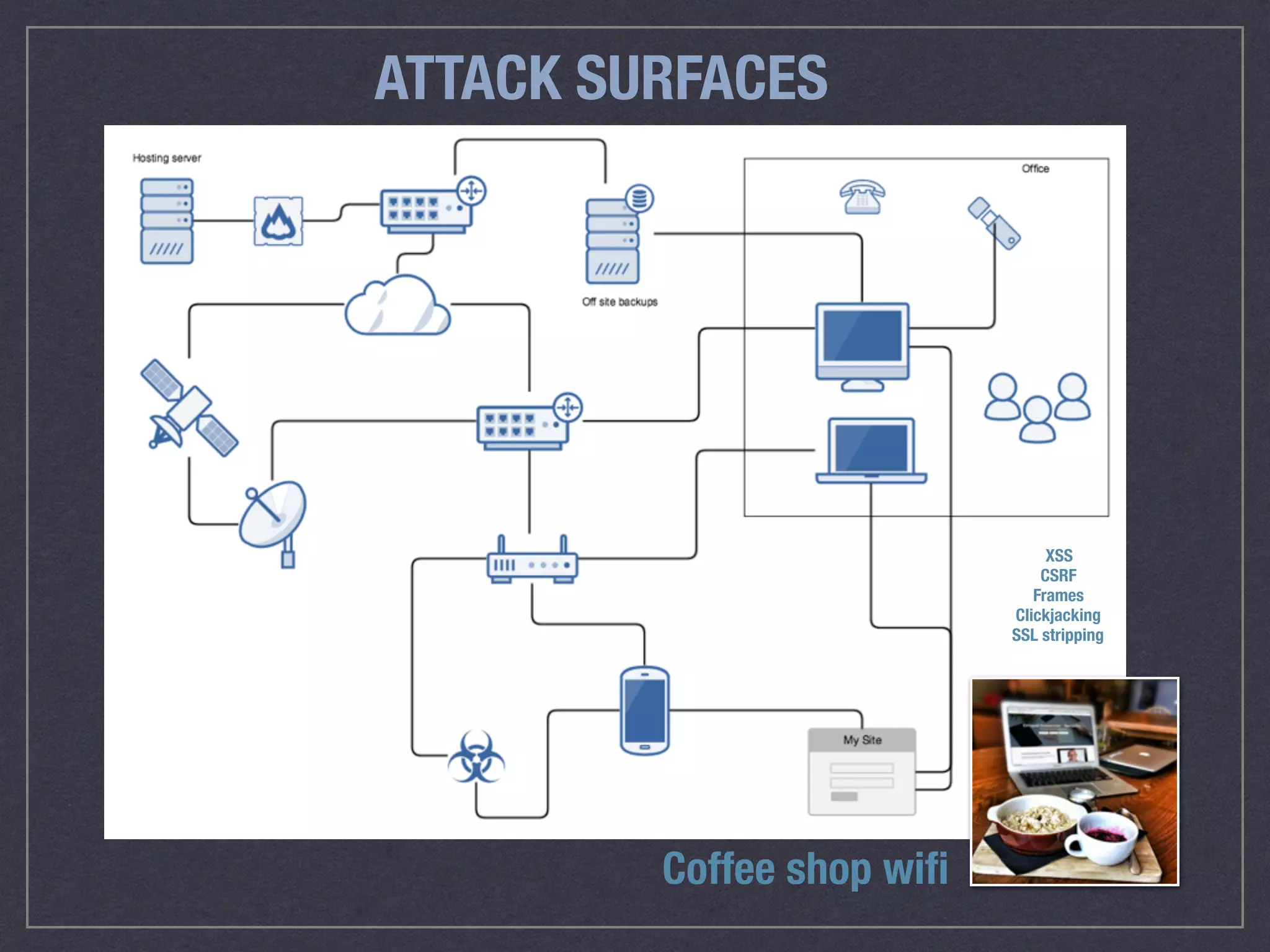
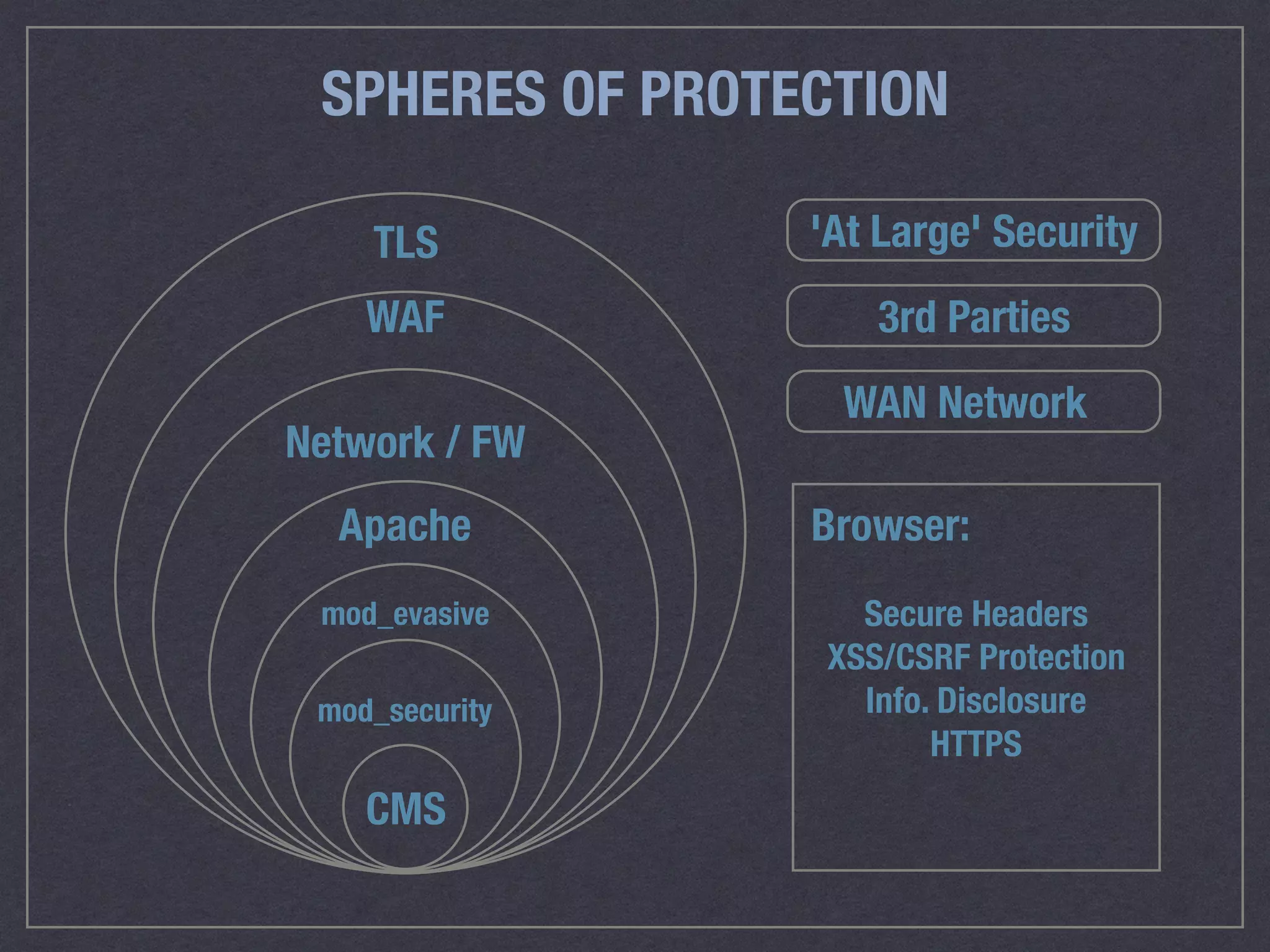
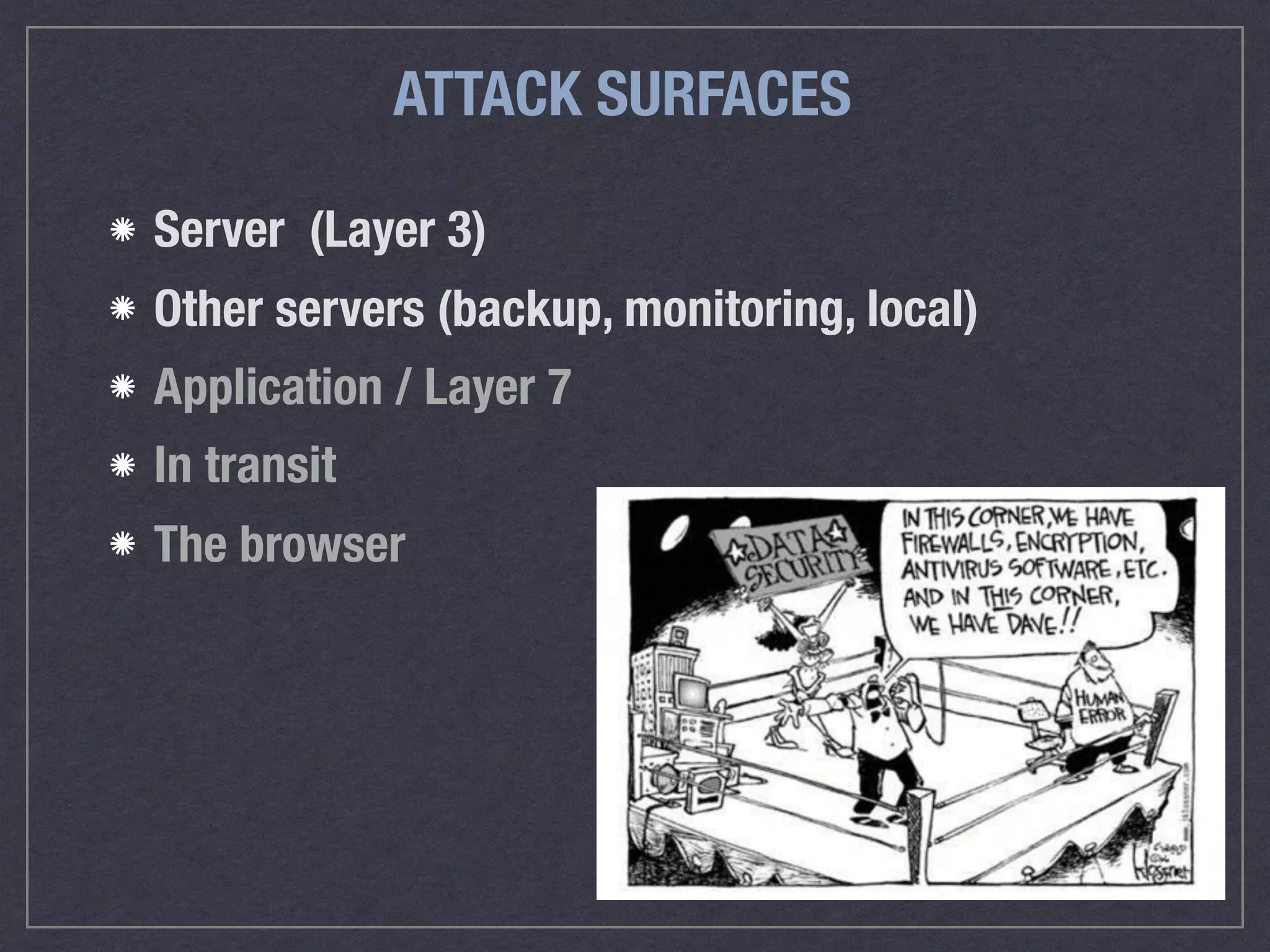
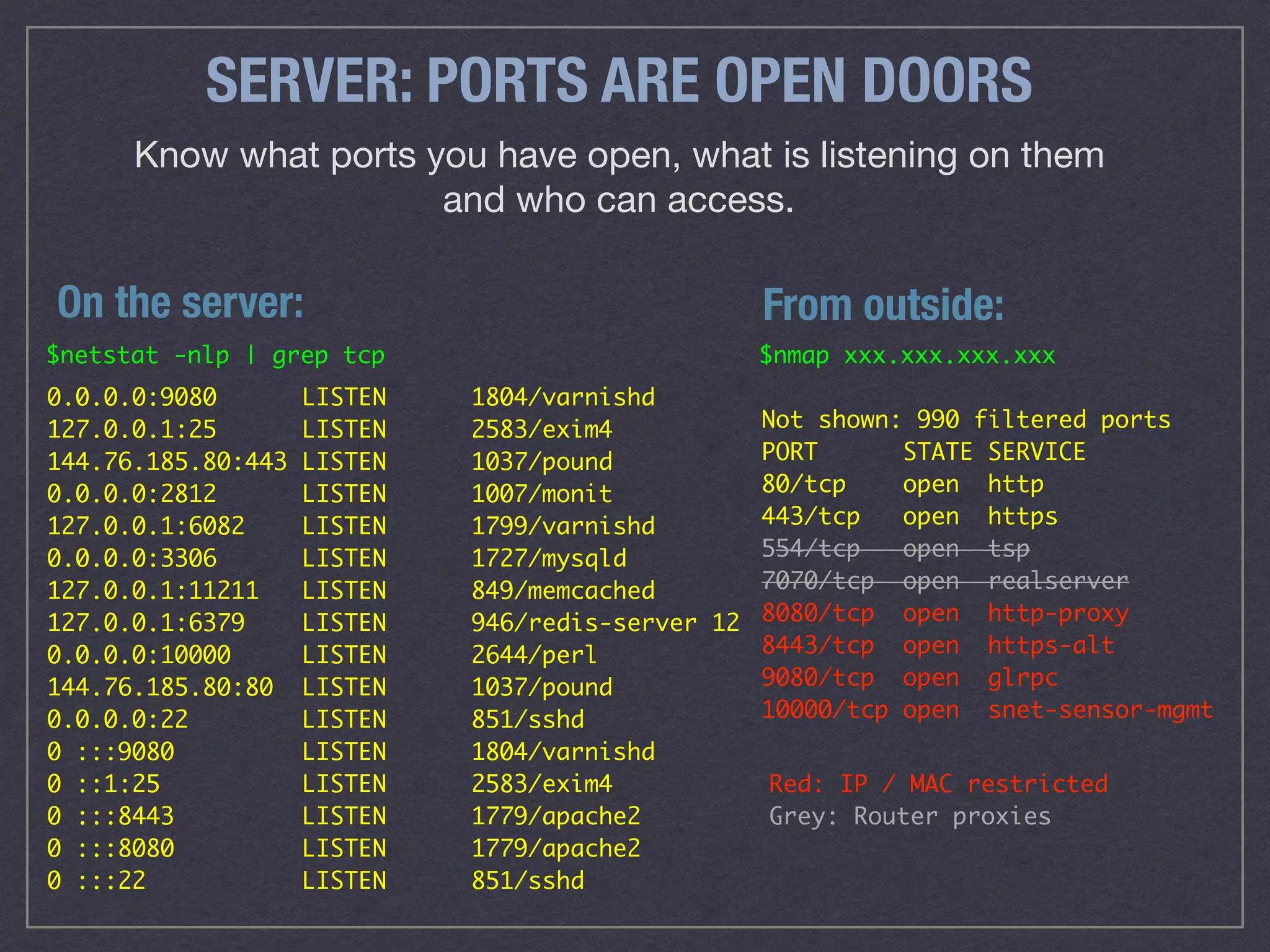
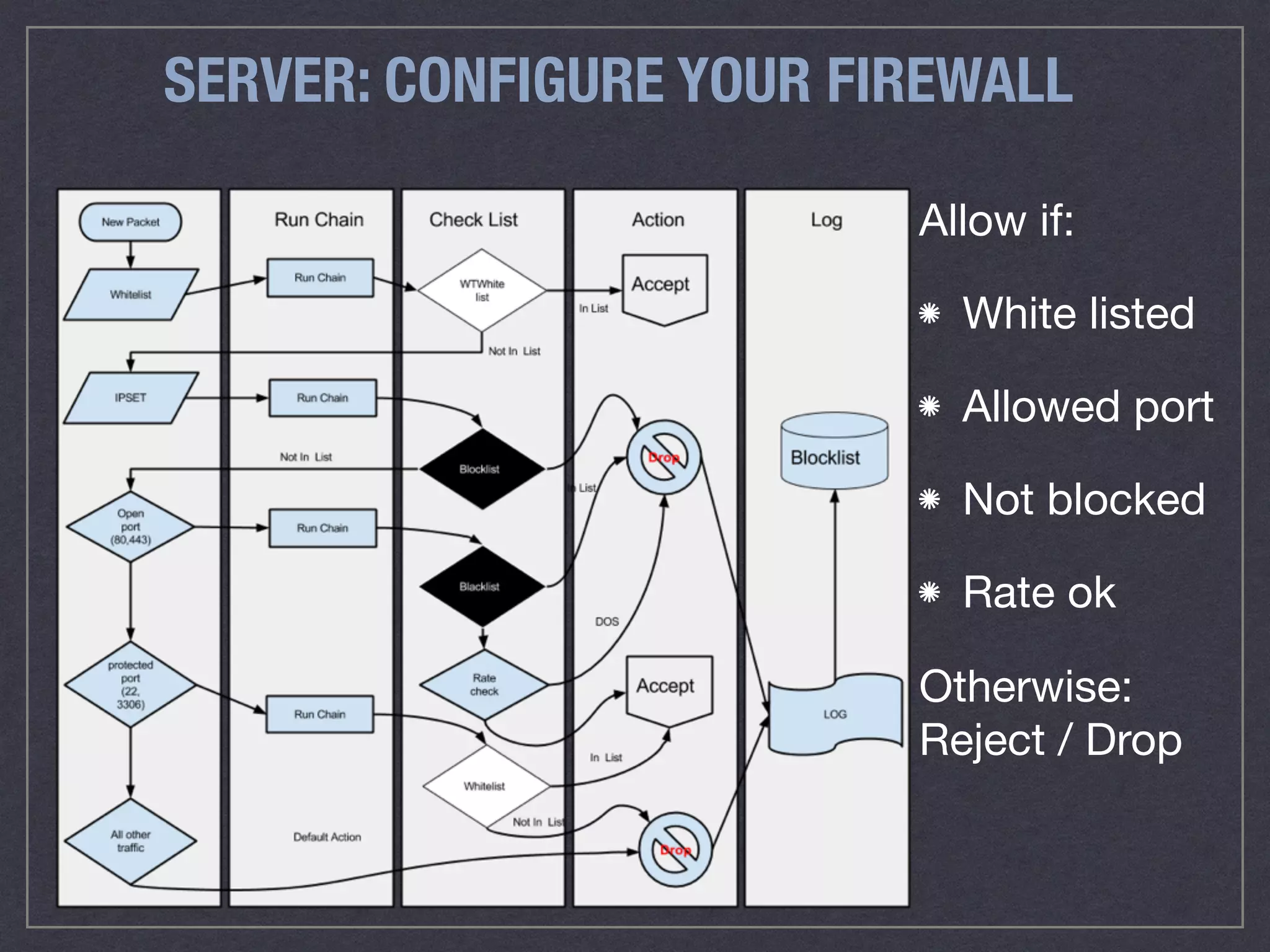
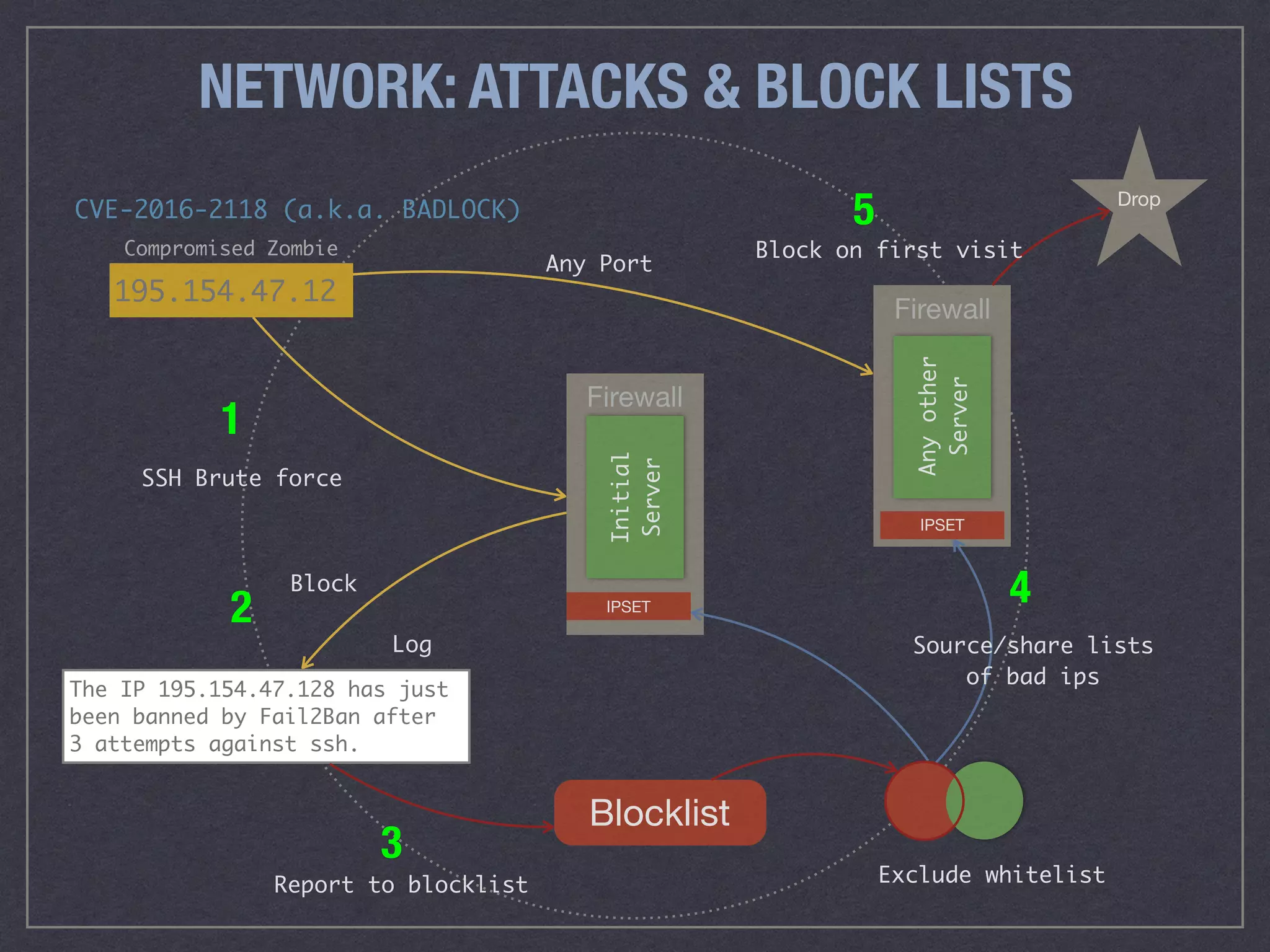
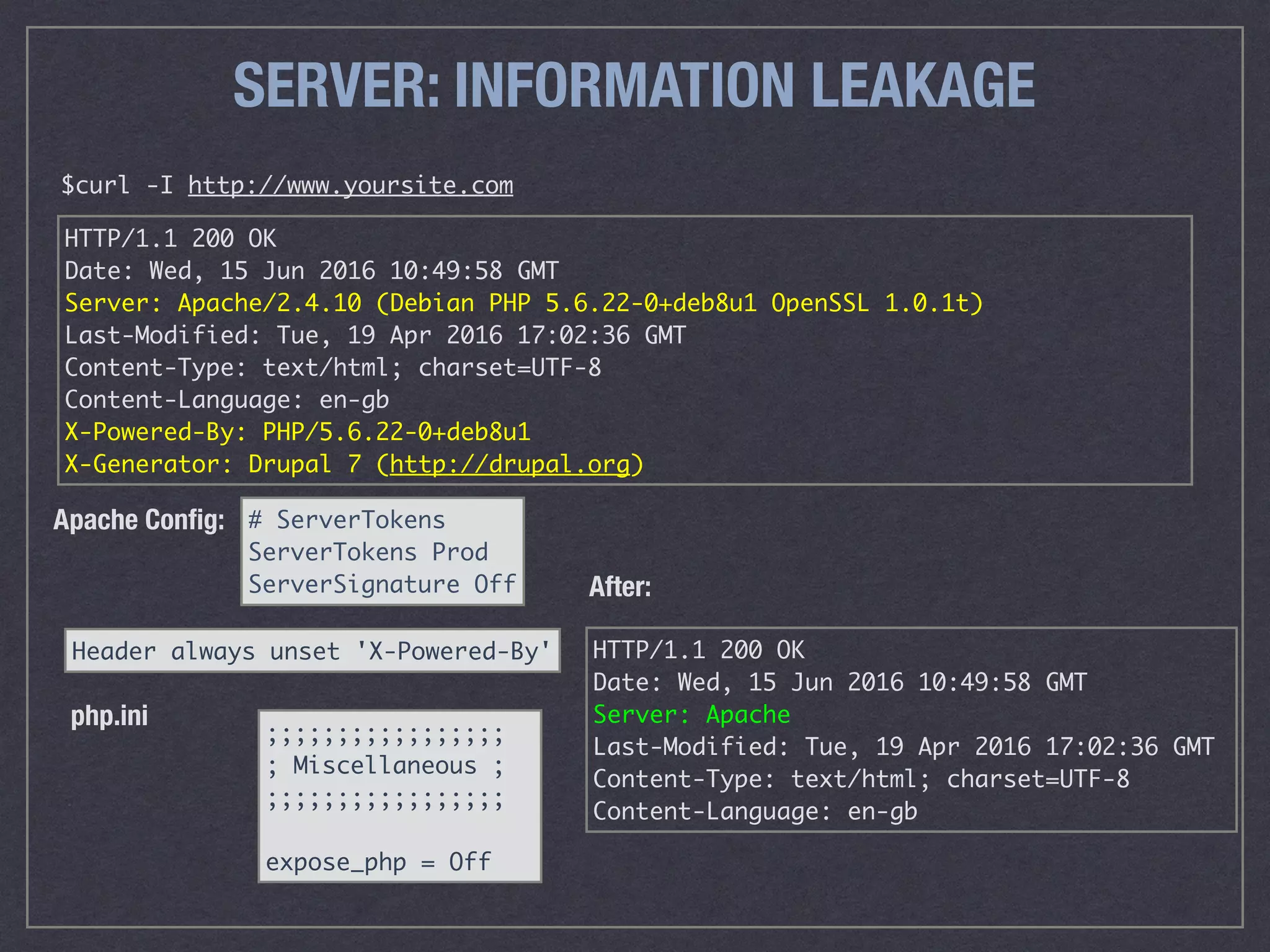
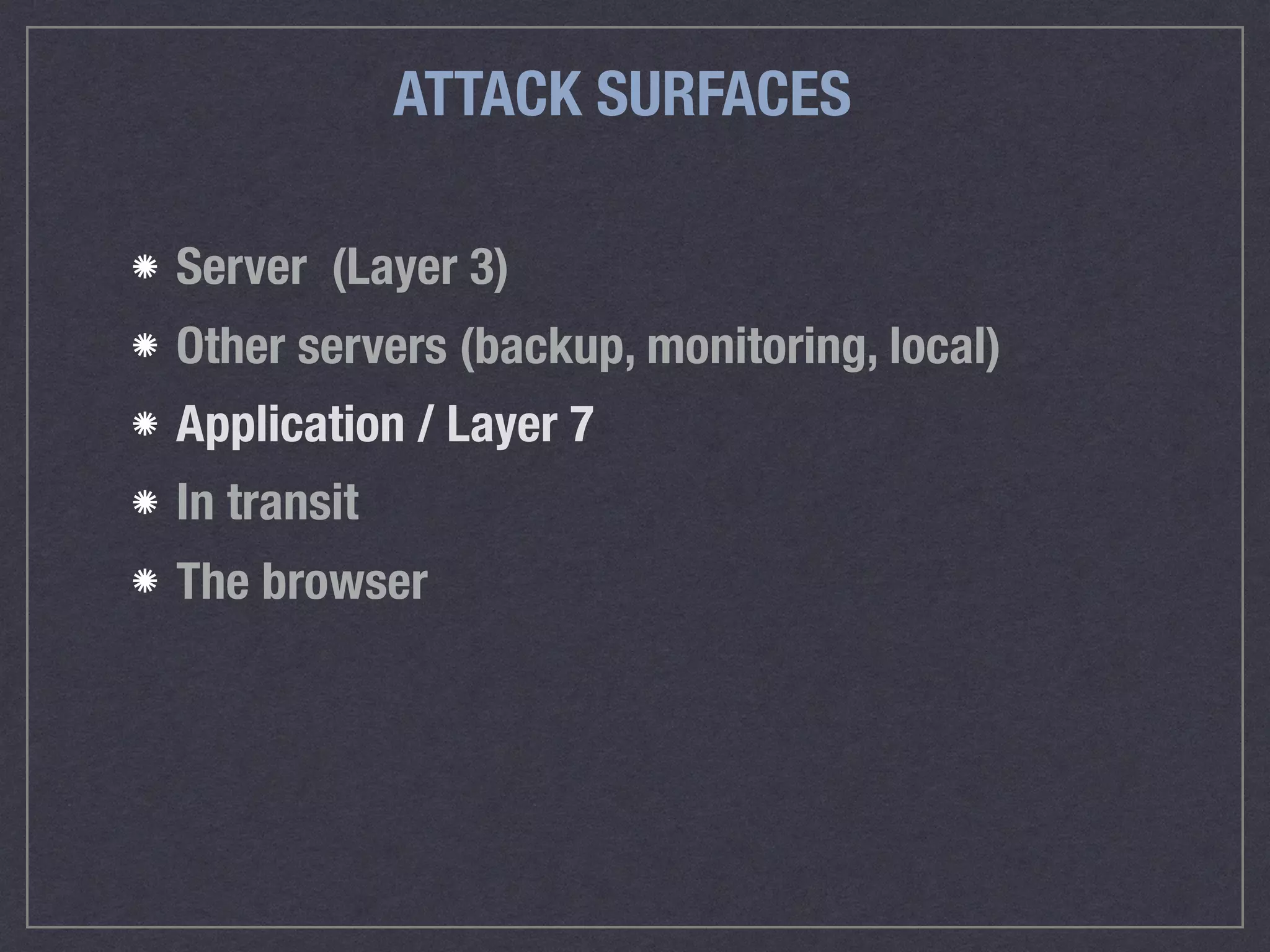
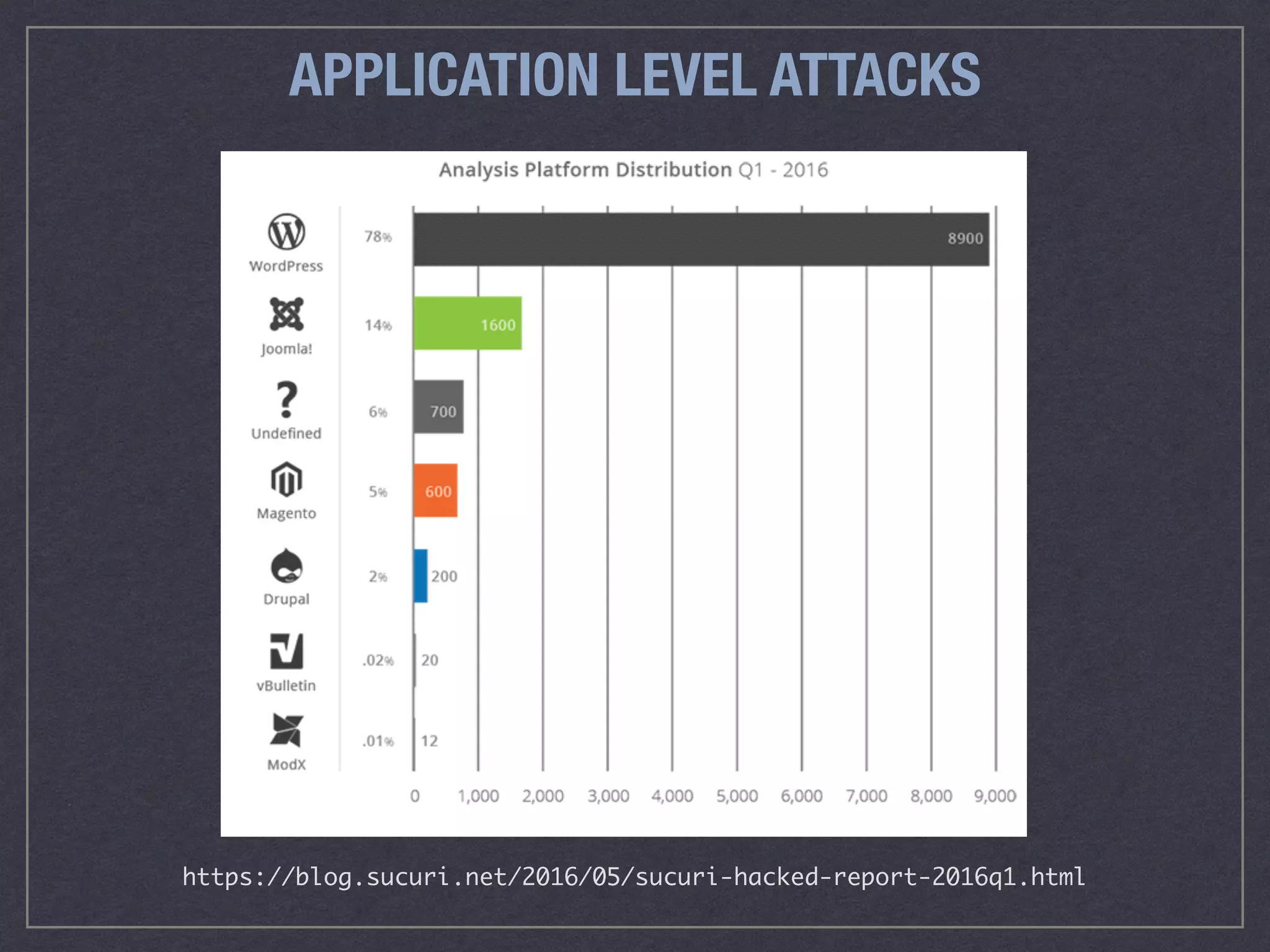
The document is a comprehensive guide on web security that outlines various threats, including hackers, malware, and data breaches, while detailing preventative measures such as server environment security, application-level security, and transport security. It emphasizes the importance of secure configurations, firewall protections, and monitoring for potential vulnerabilities and attacks. Additionally, it provides insights into browser-based attacks, security headers, and the necessity of keeping web applications and systems up to date to fend off various cybersecurity challenges.





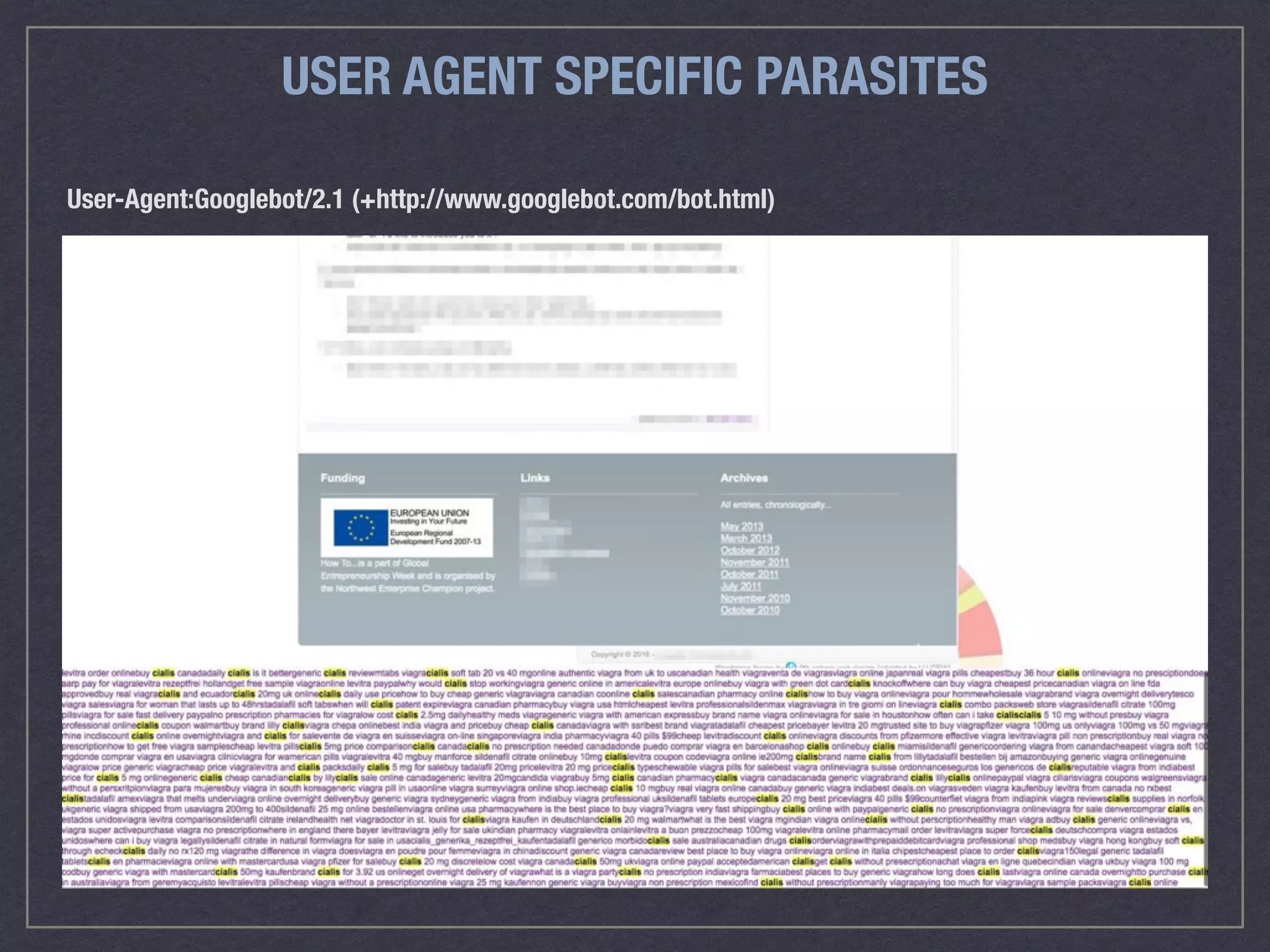
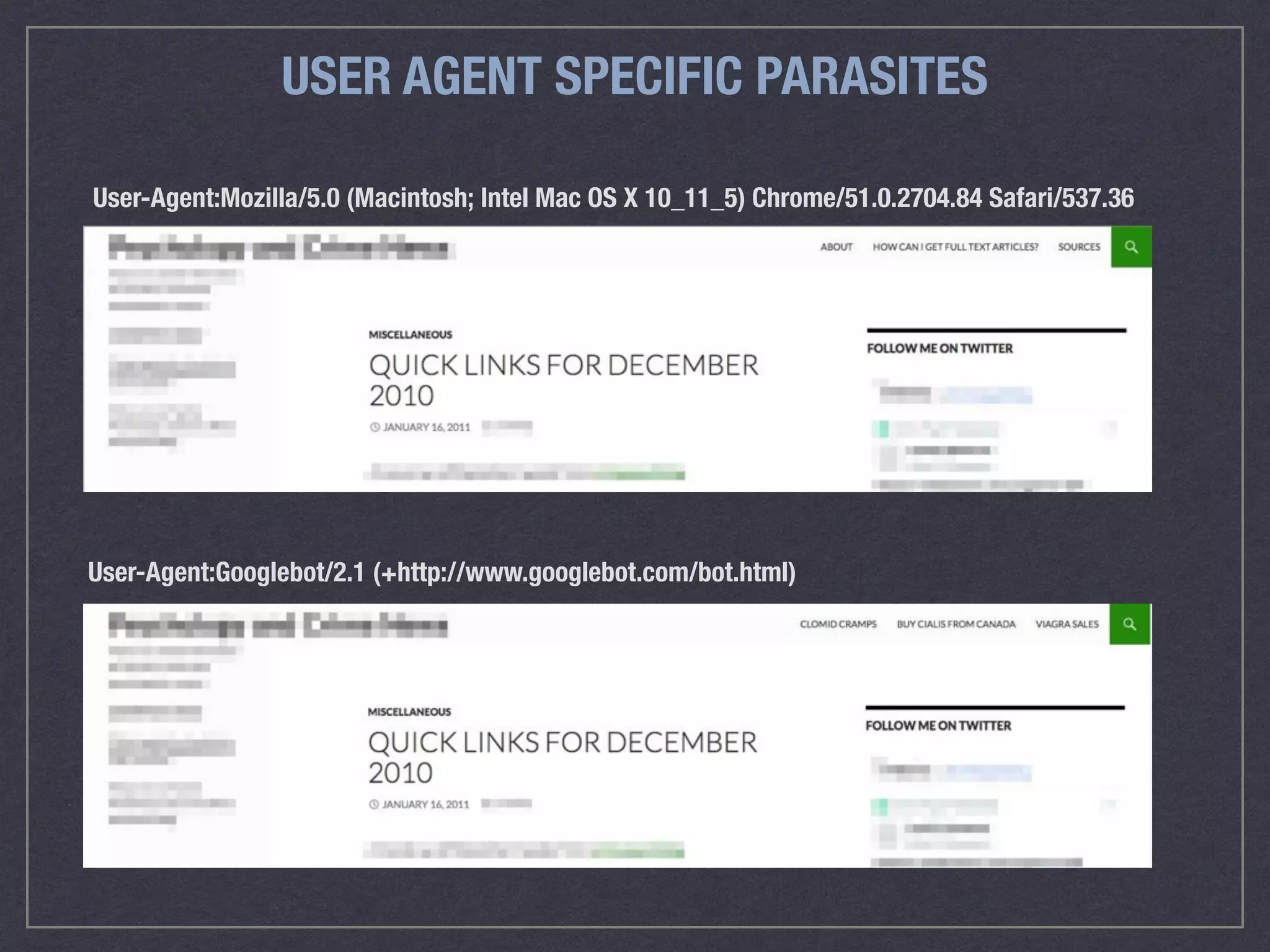


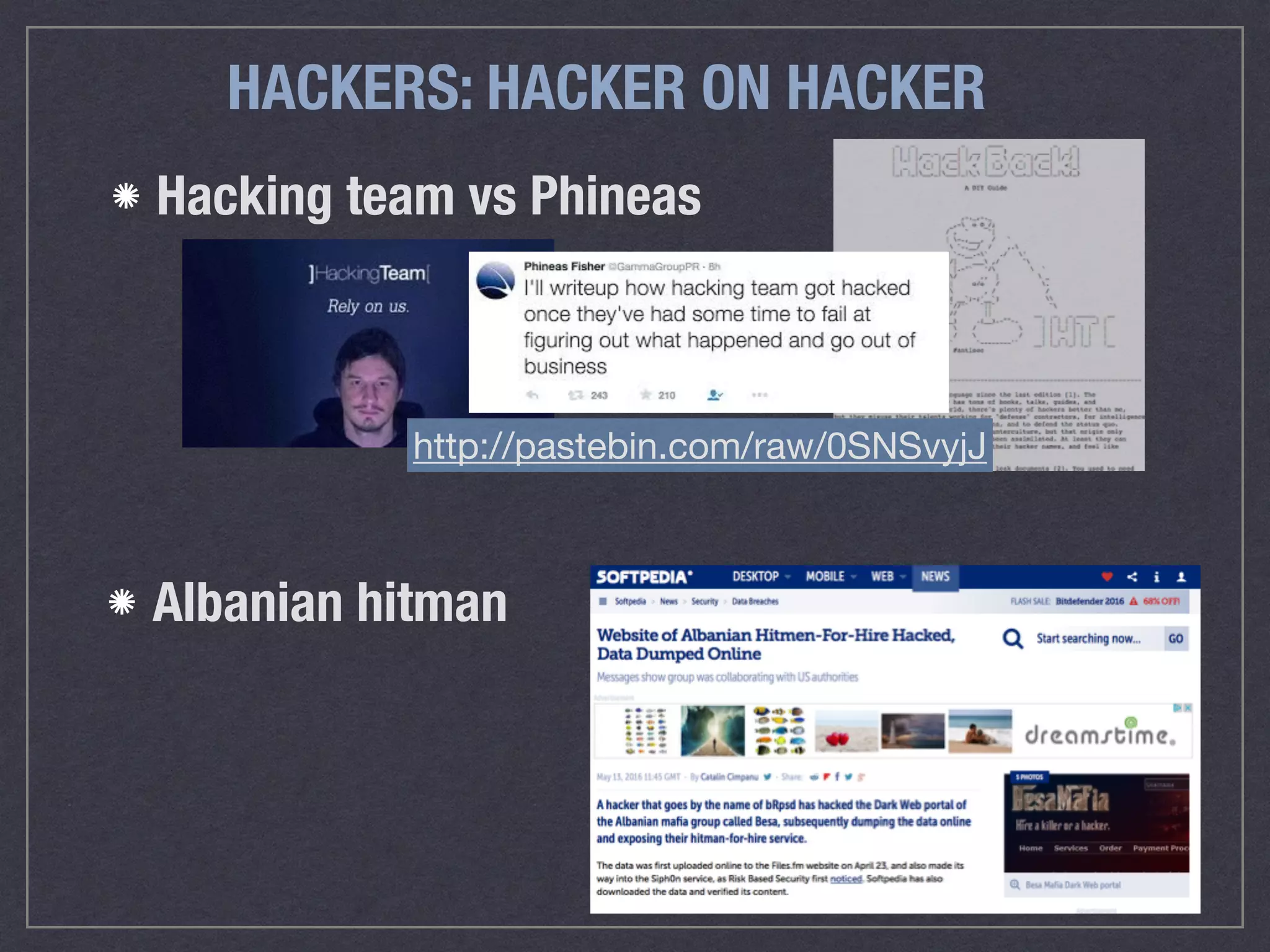







![DENY ACCESS TO SENSITIVE FILES
# Protect files and directories from prying eyes.
<FilesMatch ".(engine|inc|info|install|make|module|profile|test|po|sh|.*sql|
theme|tpl(.php)?|xtmpl)(~|.sw[op]|.bak|.orig|.save)?$|^(..*|Entries.*|
Repository|Root|Tag|Template|composer.(json|lock))$|^#.*#$|.php(~|.sw[op]|
.bak|.orig.save)$">
Require all denied
</FilesMatch>
Disallow access to files by type
Disallow access to hidden directories (i.e. git)
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteCond %{REQUEST_URI} "!(^|/).well-known/([^./]+./?)+$" [NC]
RewriteCond %{SCRIPT_FILENAME} -d [OR]
RewriteCond %{SCRIPT_FILENAME} -f
RewriteRule "(^|/)." - [F]
</IfModule>
<Directorymatch "^/.*/.git+/">
Require all denied
</Directorymatch>
.well-known
use for standard files:
favicon, DNT, letsencrypt etc
see:
https://tools.ietf.org/html/rfc5785
https://www.iana.org/assignments/well-
known-uris/well-known-uris.xhtml
https://www.drupal.org/node/2408321](https://image.slidesharecdn.com/ds-security-redacted-160725145255/75/End-to-end-web-security-45-2048.jpg)
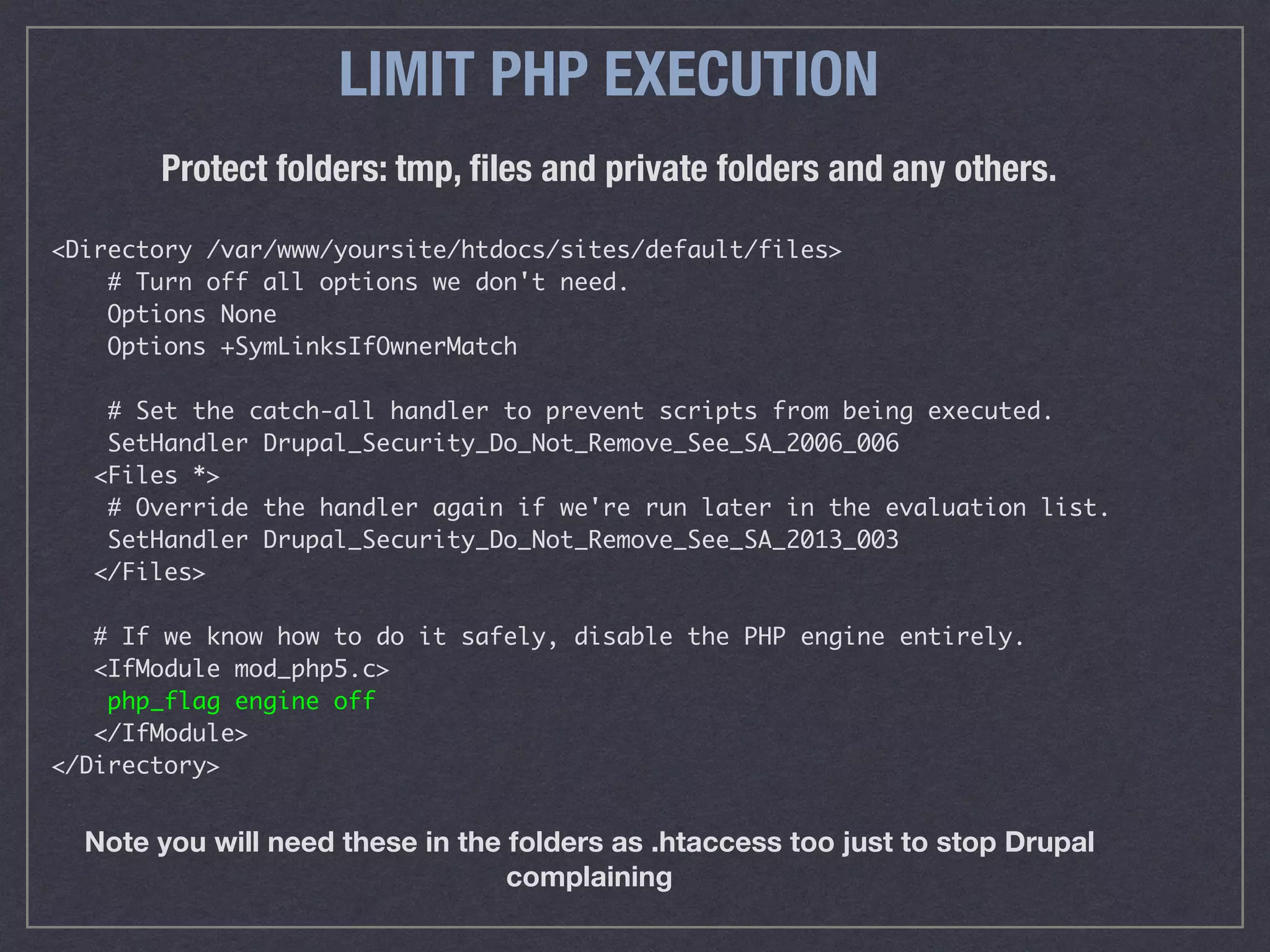
![No PHP files other than index.php
No text files other than robots.txt
<FilesMatch "([^index].php|[^myrobots|robots].*.txt)$">
AuthName "Restricted"
AuthUserFile /etc/apache2/.htpasswds/passwdfile
AuthType basic
Require valid-user
Require ip 123.123.123.123 <- Your static IP
Require ip 127.0.0.1
</FilesMatch>
LIMIT PHP EXECUTION](https://image.slidesharecdn.com/ds-security-redacted-160725145255/75/End-to-end-web-security-47-2048.jpg)